Recently, Kaspersky experts revealed that a new version of the Kelihos botnet was making the rounds, turning the computers of unprotected users into zombies. Now, the company partnered up with CrowdStrike Intelligence Team, the Honeynet Project and Dell SecureWorks, and took another crack at Kelihos.
In comparison to the old variant of Kelihos, the piece of malware that fuels the new botnet comes with some improvements in the feature department. The new Trojan can not only spread from one computer to another by infecting flash drives, but it can also steal Bitcon wallets.
On March 21, the security firms started a sinkhole operation that relied on the synchronized propagation of an IP address to the peer-to-peer network controlled by the crooks.
“After a short time, our sinkhole-machine increased its ‘popularity’ in the network – which means that big part of the botnet only talks to a box under our control,” Kaspersky Lab Expert Stefan Ortloff wrote.
After 24 hours, more than 77,000 machines were only communicating to the sinkhole. Furthermore, in order to prevent the bots from requesting new commands and to ensure that the botnet operators could no longer gain control over them, a specially crafted list of job servers was set up.
But, according to the researchers, the bad guys didn’t give up the fight easily.
“However, a few hours after we started our takedown operation, the bot-herders tried to take countermeasures by rolling out a new version of their bot,” Ortloff explained.
“We also noticed that the bot-herders stopped their network from sending out spam and DDoS-attacks. Also the botnets' fast-flux-network list remains empty since a few hours.”
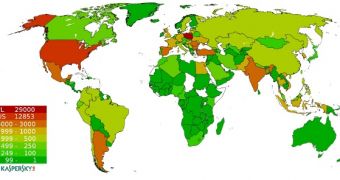
Currently, there are more than 116,000 unique bots under the security firms’ supervision, most of which located in Poland and the United States.
Note. My Twitter account has been erroneously suspended. While this is sorted out, you can contact me via my author profile.
 14 DAY TRIAL //
14 DAY TRIAL //