The Nitro campaign has been active for quite some time now, and the fact that the cybercriminals behind it have been relying on tools such as Poison Ivy and clever social engineering tricks has apparently ensured its success. Now, the attackers have added the new Java zero-day flaw to their malicious schemes.
Experts from security firm Trend Micro claim that the zero-day exploits in Java may have been taken from a Gondad, a Chinese exploit pack known to be utilized in the Nitro cyber espionage campaign.
New evidence indicates that the Java exploit may have already been utilized by the attackers for this particular operation.
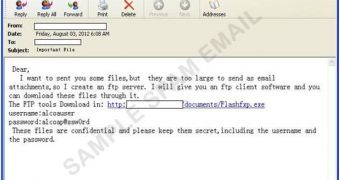
It all starts with an email which informs recipients that the sender has created an FTP server in order to send them some large files. The messages contain a link to alleged FTP client software that can be used to download the files.
According to researchers, the so-called FTP software is hosted on the same servers that store the Java zero-day and the Poison Ivy payload.
“Despite having at least two staging servers hosting the malicious files for the Java zero-day exploit (and at least three staging servers hosting executables), all the Poison Ivy payloads connect to domains that resolve to the same IP address,” Nart Villeneuve, senior threat researcher at Trend Micro, explained.
“Numerous domain names used as Poison Ivy controllers related to the Nitro campaign also resolve to that IP address.”
These clues indicate that the Java exploit was in fact leveraged in targeted attacks launched by the Nitro gang.
Fortunately, Oracle has released an out-of-band patch to address the Java issues. Companies and individuals are recommended to immediately apply it to ensure that they will not fall victims to such targeted attacks.
 14 DAY TRIAL //
14 DAY TRIAL //