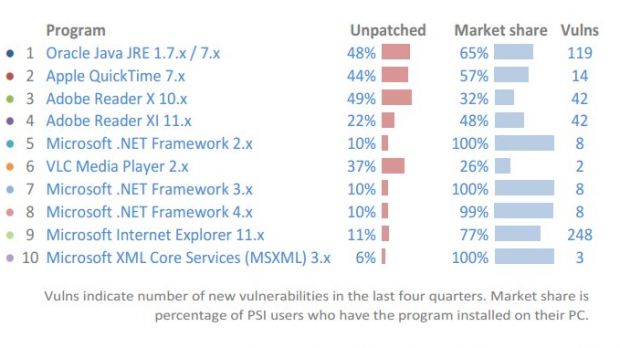
Unpatched software is the main target for cybercriminals seeking access to a user’s computer, and Java, QuickTime and Adobe Reader are the top three programs lacking the latest updates.
The security state of a computer is largely due to the software the user adds and maintaining its security requires applying the newest patches provided by all vendors, not just Microsoft.
US users need to patch programs on their systems
According to the country report for the fourth quarter of 2014 regarding the vulnerability state of machines in the United States, Java is at the top of the list of software that exposes users’ machines to unnecessary risks.
The data in the report from Secunia shows that on almost half (48%) of the US systems with Java installed, a vulnerable version was found. Apple QuickTime was detected to be outdated in 44% of the cases.
Adobe Reader 10.x appears as unpatched on 49% of the computers that have the product on the list of installed programs. Secunia says that “if 49% of PCs running Adobe Reader X 10.x, who have a 32% market share, are unpatched, 16% of all PCs are made vulnerable by that program.”
Other programs found unpatched in the US include version 11.x of Adobe Reader, Microsoft .NET Framework 2.x/3.x/4.x, VLC Media Player 2.x, Microsoft Internet Explorer 11.x, and Microsoft XML Core Services (MSXML) 3.x.
Software that is no longer maintained by developers also represents a high risk, and Secunia says that Adobe Flash Player 15.x is the most prevalent on US computers, followed by MSXML 4.x, iTunes 11.x, as well as old versions of Firefox and Chrome web browsers.
UK users are exposed through the same software
As far as users in the UK are concerned, things are slightly better, indicating that updates are applied more often.
45% of Java installations required a patch, 42% in the case of Apple QuickTime, and 43% in the case of Adobe Reader 10.x. As for the total number of PCs exposed by Adobe Reader, Secunia gives a lower number, of 13%.
Worth noting is that, regardless of parameters such as Secunia’s visibility or the market share of the products, they are the exact same ones as on computers in the US, establishing a common practice among users in the two countries.
The list of vulnerable software is fairly the same, with entries like VLC Media Player 2.x, Adobe Reader XI 11.x and Microsoft .NET Framework 2.x/3.x/4.x. The same goes for the applications that are no longer supported by their makers, Adobe Flash Player 15.x being at the top.
Secunia informs that the information published in their reports reflects the state recorded on December 31, 2014, and that new information that has become available since that date will be included in future reports.
 14 DAY TRIAL //
14 DAY TRIAL //