SophosLabs experts have identified a new piece of malware which, similar to the infamous Flashback Trojan, leverages a vulnerability in Java to infect systems. This threat is designed to target not only Mac computers, but also ones running Windows.
The Python-based malicious element is served via hijacked websites which host exploits that check if the latest Java patch has been applied.
If the system is unpatched, a piece of code, identified by Sophos as Mal/JavaCmC-A is downloaded to the affected computer.
At this point, depending on the operating system (OS), Mal/Cleaman-B is downloaded by the Java code on Windows, and OSX/FlsplyDp-A is pushed onto devices that run Mac OS X.
Unfortunately for the victims, it doesn’t end here. Once these threats find themselves on a machine that runs a Microsoft OS, they will proceed to download a backdoor Trojan called Troj/FlsplyBD-A.
On Apple systems, a Python script, update.py (OSX/FlsplySc-A), is decrypted and starts acting as a backdoor which allows the attackers to send commands, execute arbitrary code, and steal files.
Graham Cluley advises users to run an updated antivirus solution if they sense that their devices might be infected, but Mac customers can rely on another technique to perform a check.
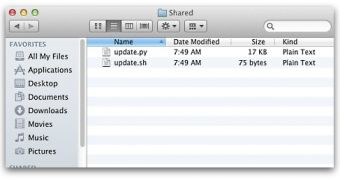
“Examine /Users/Shared/ and look for files called update.sh and update.py. update.sh is a shell script that will execute update.py, the Python script. These files can be safely deleted,” the expert explains.
After analyzing the malware’s code, researchers found a note from the developer which hints that future versions may soon be released to sport an enhanced mechanism that will help evade intrusion detection system (IDS).
Now’s probably the best time for users to patch up their Java components (or disable them altogether if they’re not needed) and install an antivirus solution if they haven’t done so already.
 14 DAY TRIAL //
14 DAY TRIAL //