Malware Domain List has reported finding a malicious Java application on the website of the Chemnitz University of Technology in Germany, infected with g01pack Exploit Kit. While this isn’t something uncommon, the fact that the Java exploit was signed with a legitimate digital certificate is.
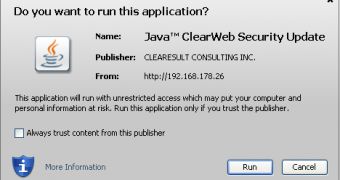
Security researcher Eric Roman has analyzed the malicious file, which poses as a “Java ClearWeb Security Update,” and found that it has been signed with a digital certificate stolen from Texas-based Clearesult Consulting, Inc.
The certificate has been revoked by Go Daddy on December 7, 2012. However, Oracle’s JAR signing and verification tool jarsigner validates the file despite the fact that the certificate has been revoked for quite some time.
In addition, the new security mechanisms implemented by Oracle don’t block signed apps unless the security level is set to “very high.”
It’s uncertain at this point if a new Java zero-day is at play here. However, it’s clear that signing a malicious application with a valid digital certificate, even a revoked one, can increase the chances for success of a cybercriminal campaign.
Oracle has released an out-of-band patch to address the latest zero-day exploited in the wild by cybercriminals and the company has promised to step up its game when it comes to security, but it’s clear that there’s a lot of work to be done.
“Cybercriminals increasingly operate in the same way legitimate businesses do; they look for the quickest and easiest means to a desired end. From Stuxnet and Flame to targeted attacks on Bit9 and Adobe, attacks leveraging digital certificates have accelerated,” Jeff Hudson, CEO of enterprise key and certificate management (EKCM) solutions provider Venafi, told Softpedia.
“The criminals have learned that leveraging flaws in the way trust is managed is among the fastest and most effective ways to infiltrate networks, take over machines, and inflict damage and steal data – without detection,” Hudson added.
“Once trust is compromised the bad guys can masquerade as whomever they want and do so undetected. Yet certificate-based attacks on trust can be completely eliminated through a few simple steps.”
In February, Venafi and the Ponemon Institute have released a study which shows that organizations risk losing $35 million (26 million EUR) every two years because of attacks on trust.
“Flame taught cybercriminals that weak certificates can be used to take control of Windows environments, and Microsoft taught the world that by removing them from the network these types of attacks can be avoided,” the CEO said.
“Why organizations aren’t taking simple management steps to inventory and replace all sub-standard certificates on their networks is beyond belief. This latest Java exploit news is another example of why effective certificate management is critical.”
 14 DAY TRIAL //
14 DAY TRIAL //