Security researchers found that some online locations with adult content in Japan have been compromised with a new variant of a banking malware that has been used in previous campaigns by threat actors.
ESET identifies this malware family as Win32/Aibatook, and they have found a new variant that is no longer written in Delphi; it appears that the malware writers switched to C++ and also implemented some changes regarding the way it was distributed, how the details were stolen and the targeted financial institutions.
The researchers say that the threat actors do not rely on entire exploit kits to infect the machines of the victims, and use instead only one exploit at a time.
This is delivered through Japanese adult websites and leverages a Java vulnerability (CVE 2013-2465). Researchers’ observations show that this distribution method has been used by the cybercriminals since the middle of April.
At least four domains have been compromised, all of them containing adult content targeting Japanese. The crooks seem to have prepared the campaign for maximum impact because some of the infected domains are among the most visited 2,000 in Japan.
Victims are directed, via a malicious link, from the adult content site to another compromised location that delivers the Java exploit.
ESET says that after the malicious file is downloaded, another file, named “counter.php,” is requested from another domain.
“We believe this last step is related to the conditions under which the HTML snippet will be inserted: only a limited number of users per day will receive the exploit, explaining the need to count the number of tries. This counter script is hosted on what appears to be yet another compromised website, ‘ccc.rejec.net’,” says the research team in a post.
It appears that the cybercriminals have integrated two different methods for stealing the financial credentials from the infected computers of the victims.
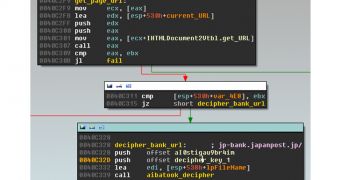
In the case of a smaller number of targeted banks, Japan Post and SBI Sumishin Net Bank among them, they use a custom method, while for the gross of the financial institutions, about 90 of them, a more generic one is employed.
However, according to ESET, both of them are leveraged by manipulating the Internet Explorer web browser through the IHTMLDocument2 interface, which offers read/write permission for web pages with high-level methods.
Modification of the web pages is used for the small number of targeted banks, whose addresses are hard-coded in the malware, in order to obtain as much information from the victim as possible.
The generic information stealing method has been refined in time and relies on “form-grabbing,” a technique that monitors the input fields used by the victim and sends the entered details to the command and control server of the crooks.
ESET team said that Win32/Aibatook, an earlier variant also being analyzed by Symantec, has been developed on a constant basis in the past months. They believe that its distribution is very likely to widen in the near future.
 14 DAY TRIAL //
14 DAY TRIAL //