F-Secure researchers have come across an interesting piece of malware designed to target Mac devices. The most surprising thing about Backdoor:Python/Janicab.A is that the file that hides the malware uses the right-to-left override (RLO) character to mask its extension.
The Unicode RLO character is designed to support languages that are written right to left, such as Hebrew or Arabic. However, malware developers have been abusing it to mask the extensions of malicious files.
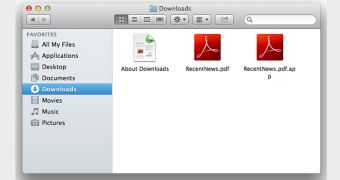
In the case of the Mac malware analyzed by F-Secure, the malicious file has the .app extension (RecentNews.fdp.app). However, because the RLO trick is used – the Unicode character is placed before the “f” –, the file becomes RecentNews.ppa.pdf.
Once it’s launched, the malware drops a decoy document. In the meantime, it creates a cron job for its launch point, and a hidden folder where it stores its components.
The malware gets its command server’s address from YouTube videos and other websites.
Its main goal is to take screenshots and record audio by using a third-party application called SoX.
Janicab.A is written in Python, it uses py2app for distribution, and it’s signed with an Apple Developer ID.
 14 DAY TRIAL //
14 DAY TRIAL //