JamieOliver.com has been compromised once more with malicious code that redirects to Fiesta exploit kit (EK), which exploits vulnerable versions of browser plugins Flash and Java.
This is the third time the website has been infected this year, as the first time happened in February and then again in March; Fiesta was present in both cases.
Same malicious code used on torrent indexing site
One of the two payloads is not widely detected by antivirus engines available at Virus Total, as only four products raised the red flag. In the case of the other threat, the detection rate is much better, with 11 antivirus engines labeling it as malicious in a scan on Sunday.
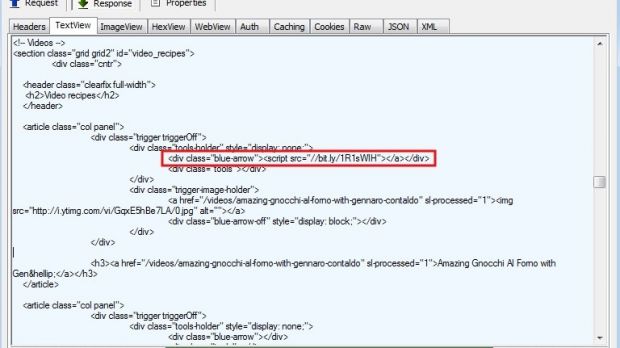
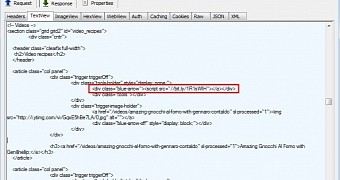
Jérôme Segura from Malwarebytes analyzed the compromise and says that the malicious code redirecting to the browser-based attack tool is not delivered via a rogue advertisement, but instead it is injected in every page of the website.
He says that the code is almost identical with the one found earlier this month in an attack targeting popular torrent indexing website SubTorrents.
In a blog post on Tuesday, Segura said that, once the payload is executed, it resorts to the PowerShell command line utility in Windows to achieve persistence on the system.
Fileless password stealer seems to be the payload
Judging by the method used by the malware, it is possible that the cybercriminals spread Gootkit, a clone of the fileless Poweliks, which resides in the memory of the computer to evade detection.
The administrators of JamieOliver.com have acknowledged the issue and are currently working to clean up the website.
As far as users are concerned, they are highly recommended to install the latest updates for the browser plugins, since this is the reason drive-by attacks such as this one are successful.
Drive-by attacks are particularly efficient because they do not raise any suspicions. If the EK finds a vulnerable plugin, it exploits it and delivers the payload without the user being aware of the activity.
 14 DAY TRIAL //
14 DAY TRIAL //