A malicious email campaign relying solely on social engineering delivers messages to users in Italy and Spain containing links to ransomware with file encryption capabilities, researchers have discovered.
The cybercriminals seem to aim at users in these two countries in particular because traffic coming from different geographical locations is delivered to a legitimate Google domain by a redirect server.
Malware is hosted on a cloud storage account
Researchers at F-Secure caught samples of the malicious emails and started to analyze how victims’ computers received the crypto-malware.
Without running the connection to the redirect server from one of the two countries, the payload (identified as a variant of Cryptowall or Cryptolocker) is not delivered to the victim.
“Well, we noted that the first two URLs were PHP. Since PHP code is executed on the server side, not locally on the client, it is possible that the servers were 'deciding' whether to redirect the user to Google or to serve malicious content, based on some preset conditions,” F-Secure says in a blog post published on Tuesday.
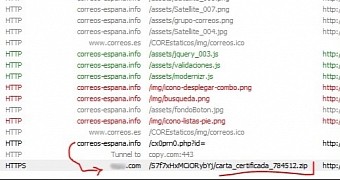
The malware is stored on an undisclosed cloud storage server, which is reached from the link provided in the malicious email.
Users in Spain have to solve a CAPTCHA challenge
To lure the users into downloading the malware, the cybercriminals resort only to social engineering, as the email purports to be from a delivery service (courier or postal). It is claimed that a parcel awaits to be collected and a link is offered to track the alleged package on its route to its destination.
The researchers say cybercriminals implemented a CAPTCHA challenge in the case of the messages sent to Spanish users, to make the entire affair more credible.
They add that file encryption procedure particular to this sort of threats occurs only if the user downloads and executes the files manually.
This approach may ring the alarm and spare users some unnecessary trouble, although chances are that most of them will fall for the trick.
To avoid facing crypto-malware aftermath, users should create backup copies, at least for the most important files, and store them in a location as isolated as possible from the main computer.
 14 DAY TRIAL //
14 DAY TRIAL //