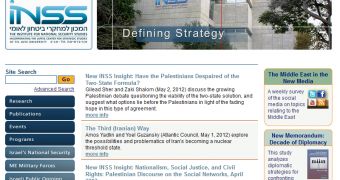
It’s well known in the security community that Israeli websites have been under constant attack in the past few months. One of these attacks seems to have targeted the Institute for National Security Studies (INSS), whose website has been altered to serve visitors the infamous remote administration tool (RAT) known as Poison Ivy.
Websense experts found that the infection leverages the same Java exploit vector that’s currently used by the Flashback Trojan to spread on Mac OS X machines.
The INSS is an independent organization that studies Middle Eastern issues and Israel’s national security. This is what leads experts to believe that the INSS site may not be a random target, but one that’s part of an operation meant to infect the computers of individuals interested in national security related topics.
The infection starts when the site’s main page is opened. The JavaScript that has been injected into the webpage loads a Java file which holds the exploit of the CVE-2012-0507 vulnerability.
The cybercriminals responsible for hijacking the site deployed a number of methods designed to ensure that security products and malware analysis technologies would not raise any alarms when scanning the site.
To avoid being detected, they obfuscated the malicious code and they embedded a 104 megabyte text file into the Java file. The latter technique is utilized because malware scanners in many cases ignore large files, since it is known that malicious elements tend to be small in size.
Unfortunately, the site’s webmasters haven’t responded to Websense’s notification regarding the issue. That means that users who want to visit the site and don’t have the latest Java updates installed, or decent antivirus software, can almost instantly become victims.
 14 DAY TRIAL //
14 DAY TRIAL //