Cyber-attacks are becoming more common and they're growing in both intensity and frequency, making it more important than ever to use the best protection out there to ensure that networks are secure.
Last year, for instance, Target became the victim of one of the biggest data breaches in history. The details of over 40 million credit and debit cards were stolen, and 70 million people had their records stolen, including names, addresses, emails and phone numbers. The effect was immediate and Target's profits dropped 46 percent within the first trimester.
Along with this huge security issue, it became obvious that network segmentation as a security best practice was growingly important.
Reuven Harrison, Chief Technology Officer and co-founder of Tufin Technologies, has agreed to chat with Softpedia and explain a few key points about network segmentation and how it can help.
Tufin Technologies is a network security company that specializes in management of next-generation and network layer firewalls, routers, switches, and more. The company was born in 2005 thanks to Ruvi Kitov and Reuven Harrison and has grown to work with over 1,400 customers in all areas.
Softpedia:
First off, tell us something about who you are and the company you work for.
Reuven Harrison: Tufin helps companies automate and accelerate network infrastructure changes while maintaining security and compliance. As the market leader of Security Policy Orchestration, Tufin’s award-winning Orchestration Suite gives IT organizations the power and agility to enforce security policy across complex, multi-vendor enterprise networks.
With more than 1,400 customers worldwide, Tufin enables IT to positively impact the entire business by reducing the time and cost to implement network changes by up to 80 percent.
Explain for our readers how network segmentation works and why it is growingly important for more companies to adopt this for their own businesses.
As background, network segmentation is the practice of separating networks with systems containing sensitive information from those that do not. It has become a well-known best practice for improving network performance and security. Typically, networks are segmented based on risk, compliance requirements and as a general best practice.
The idea is that if an attacker gains access to the network, say via stolen user credentials, access (and damage) is limited to a subset of systems. With proper network segmentation, organizations can greatly reduce the impact and breadth of security breaches.
With firewalls typically segmenting the network within the enterprise, network segmentation oftentimes creates management complexity because firewalls have long and complex rule bases, which open the door for human error. A security admin might make a policy change that accidentally impacts their organization’s segmentation without even realizing it. As a result, automation is needed to ensure network segmentation is preserved during any change request.
However, in many organizations, network segmentation has been a “set it and forget it” effort, which once done is almost immediately out of date. Network segmentation needs to be managed, and policies continuously enforced to maintain the desired network segmentation. Security is not the only issue addressed by proper network segmentation. The ability to contain network problems, improve performance, and reduce congestion are all key benefits that come from a well-segmented, well maintained network.
Today’s IT organizations must re-evaluate how they approach network segmentation and adopt the tools and methods required for proper network segmentation management.
Tufin recently announced the Unified Security Policy. Tell me more about this. How will it help companies? Most organizations are currently managing network segmentation by manually tracking firewall and router configurations, others use spreadsheets. However, with the complexities of today’s networks and the constant changes coming from the business, maintaining the desired network segmentation is practically impossible.
Tufin’s first-in-kind Unified Security Policy™ takes a business process approach to network segmentation based on risk and compliance factors. It allows organizations to control their actual versus desired network segmentation, highlighting policy violations before a change is made on the network so as not to break compliance or expose the network to unnecessary risk.
We first introduced this capability into the Tufin Orchestration Suite in February 2014, but this latest version of the Tufin Orchestration Suite (Version R14-2) extends Tufin’s Unified Security Policy into SecureChange®, its Network Change Automation platform, giving security managers the ability to maintain tight control over network segmentation, preserving the desired network segmentation during the change process. The result is that even in the case of highly complex environments, intelligent automation makes it possible to have strong security without sacrificing business agility.
This new version also includes central violation and exception management resulting in comprehensive audit ability and documentation, as well as reduced network exposure.
Now, security managers can easily allow and manage exceptions over time in a secure, complete fashion, tracking and recertifying exceptions upon expiration. By eliminating the complexity associated with managing network segmentation, our customers can automate best practices for network architecture into their daily operations, without losing control of the process.
What types of attacks can network segmentation fend off and how well insulated are these?
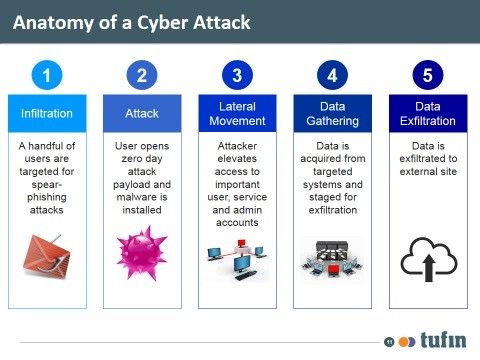
When looking at how network segmentation can fend off attacks, you must go back to how network attacks usually happen (or the anatomy of a cyber-attack). Below are a few of the scenarios our customers contend with regularly:
Where network segmentation comes into play is mainly on steps 3 and 4 of an attack. Good network segmentation can dramatically minimize the ability of an attacker to perform a lateral movement in the network.When access between network zones is limited (only to what is really needed by the business), attackers will find it hard to move from a compromised server/desktop to more restricted networks, where the target data is usually found. Furthermore, good network segmentation can also limit an attacker’s ability to do data gathering. Again, when access between networks and zones is limited, an attacker will find it very hard to copy data between restricted networks to unrestricted networks as a preparation for infiltration.
So to summarize, good network segmentation cannot eliminate attacks completely, but can contain and limit them to the immediate compromised network, minimizing the effect and damage that an attacker can cause.

 14 DAY TRIAL //
14 DAY TRIAL //