Exploit mitigation techniques available in Internet Explorer keep the browser strong in face of memory exploits, but attacks could be carried out through the script interpreter engine.
In a blog post from network security firm Fortinet security researcher Zhenhua Liu explains how exploit researchers may have opened the box of Pandora as far as the safety of Microsoft’ browser is concerned.
He shows that scripts can be as efficient as a shellcode and that malicious scripts can be run by script interpreter engine on a target machine with escalated privileges, based on the discoveries of Yang Yu (CanSecWest 2014 presentation), Yuki Chen and Yuange (Chinese).
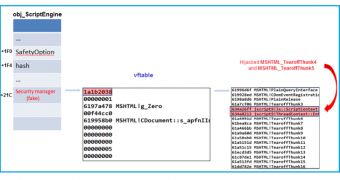
Liu says that “the safety of the IE script engine relies solely on one single byte - the SafetyOption flag.” Getting elevated privileges requires modifying the flag to 0 (zero) or in JScript and 0 (zero) in VBScript.
The COleScript::CanCreateObject and ColeScript::CanObjectRun are the functions that perform separate checks on the SafetyOption flag to decide if it is safe to create and run a given ActiveX object.
Penetrating the protection layers is not that simple, though. For the trick to work, the attacker needs to know the memory address of the flag, hence full process memory access is required, which is not actually impossible (zero-day vulnerabilities still continue to pop up).
On the other hand, if full process memory access has been gained, the attacker can modify the SafetyOption flag and execute malicious scripts with elevated privilege.
The researcher warns that the exploit model works with Internet Explorer 11, too, but the flag can only be modified in VBScript because the protection for the JScript engine has been strengthened by introducing a 0x20-byte hash value.
As such, when “the SafetyOption flag is used, the function ScriptEngine::GetSafetyOptions is called to generate a new hash that is then compared with the original hash value, which is stored in memory.”
However, it appears that the two functions checking the flag for permission are still responsible for enabling elevated privileges and even if SafetyOption returns a non-zero value, the action can be completed by modifying the application data in the ScriptEngine object.
The researcher predicts more zero-day vulnerabilities to appear, “Since the only prerequisite for using this is a vulnerability for an arbitrary write (which is common nowadays), we can anticipate more zero-days that will use this technique in the near future.”
He applauds the fact that in edge mode, Internet Explorer 11 does not support VBScript and suggests better security of the JScript engine (referring to the member data in the object and disabling some privileged methods), along with “implementing randomization in the IE custom heap management.”
 14 DAY TRIAL //
14 DAY TRIAL //