Security researchers from the University of New Haven Cyber Forensics Research and Education Group (UNHcFREG) have been analyzing the popular instant messaging application Viber.
They’ve found that the images, doodles, videos and location data sent by Viber users are not encrypted. An attacker can easily gain access to the information by launching a man-in-the-middle (MITM) attack.
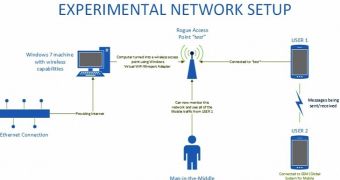
To test their findings, experts have set up an experiment using an HTC One smartphone running Android 4.4.2, a Samsung Galaxy S4 with Android 4.3. The tests were conducted on Viber 4.3.0.712. Traffic was captured using common tools like NetworkMiner, Wireshark, and NetWitness.
“The mobile traffic was captured using the Windows 7 virtual wifi miniport adapter feature. The host computer was connected to the Internet via an Ethernet cable so that the wireless card was not in use. The Ethernet connection was set to share its Internet access with the virtual wifi miniport adapter,” experts noted about their experiment.
So what exactly have the experts found? In addition to determining that images, doodles, videos and location images are unencrypted when they’re sent, they’ve also found that the data is stored on the Viber Amazon Servers in an unencrypted format.
Furthermore, the data stored on these servers is not deleted immediately and it’s easily accessible without the need for authentication credentials.
“Simply visiting the intercepted link on a web browser gives us complete access to the data,” the experts noted.
UNH researchers have notified Viber, but they haven’t heard back from the company’s representatives. On the other hand, Viber appears to be aware of these flaws.
“This issue has already been resolved. It is currently in QA, and the fix will be released for Android and submitted to Apple on Monday. As of today we aren't aware of a single user who has been affected by this,” the company’s representatives told CNET.
This isn’t the first time security experts from the University of New Haven find such issues in popular instant messaging applications. Earlier this month, they found that WhatsApp sent location data without encrypting it. Similar to Viber, WhatsApp also promised to address the issue with an upcoming release.
While such types of vulnerabilities are not critical, it’s important that companies encrypt all communications as much as possible.
Check out the proof-of-concept video published by the University of New Haven Cyber Forensics Research and Education Group:
 14 DAY TRIAL //
14 DAY TRIAL // 