JustSystems, the developer of the popular Japanese word-processing application Ichitaro, has published updates to address a vulnerability that has been exploited in the wild.
Symantec researchers say they had spotted attacks leveraging the zero-day flaw since September 2013. However, at the time, they couldn’t reproduce the exploit in their testing environment.
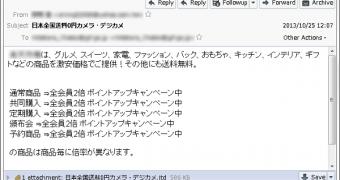
The attacks start with a fake email that carries what appears to be a harmless Ichitaro file. In order to trick recipients into opening the attachment, the notifications purport to come from a popular Japanese online shopping website, and they promise all sorts of bonuses, such as extra points and free shipping.
When the malicious attachment is opened, the targeted system becomes infected with Trojan.Mdropper. The cybercriminals have been using Trojan.Mdropper to drop Backdoor.Vidgrab. The same threat had been utilized as a payload in the recent watering hole attacks that leveraged the CVE-2013-3893 Internet Explorer vulnerability.
Experts believe that it’s either the same malware group behind both attacks, or two teams that are somehow connected. Backdoor.Vidgrab has been mainly seen in cyberattacks aimed at government sectors in the Asia-Pacific region.
Interestingly, Symantec has found a connection between Trojan.Mdropper and the notorious Chinese state-sponsored group dubbed APT12. Researchers have a number of theories.
“The attackers, possibly belonging to the APT12 group who may have also developed BackdoorVidgrab, are persistently targeting similar, if not the identical, targets by attempting to exploit Ichitaro. The attackers may also be using the targets as guinea pigs to test if the exploit code works properly,” Symantec noted in a blog post.
“The attack may also be a precursor, the attackers could have run the tests in order to find effective email contents and subject lines, for example, that are enticing enough lure targets into opening the malicious attachment.”
 14 DAY TRIAL //
14 DAY TRIAL //