A cybercriminal campaign relying on the Xtreme Remote Access Trojan (RAT) has been seen targeting high-profile organizations from Israel, Palestine, but also other countries such as the US, UK, Turkey, Macedonia and Slovenia.
One of the victims of this campaign is an Israeli police force that has had to disconnect all its computers from the Internet after finding the Xtreme RAT on one device.
At the time, experts revealed that the agency’s employees were tricked into installing the malicious element with the aid of spoofed emails apparently coming from Binyamin Gantz, the current chief of general staff of the Israel Defense Forces (IDF).
Security researchers from Seculert reveal that the same cybercriminals have sent an email to Jonathan Klinger, an Israeli political candidate.
The email he received appeared to be coming from an IDF spokesperson. However, this time around, the message did in fact come from a legitimate email address.
The Gmail account of the IDF spokesperson was hacked by the attackers and utilized to send out spear-phishing emails to victims.
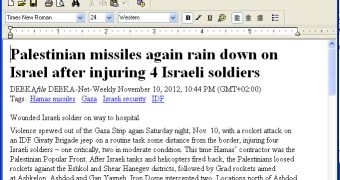
The messages sent out by the cybercriminals relied on the same strategy as before. They contained Word documents with reports on political matters – in this case, it was related to Operation Pillar of Defense.
When the victim launched the attachment, the malware stepped into play. In the meantime, a real document was opened to avoid raising suspicion.
This particular Xtreme RAT variant has been found to communicate with a command and control (C&C) server located in the United States.
As experts emphasize, it’s not uncommon for cybercriminals to utilize political events in their campaigns. However, the fact that email accounts are hijacked and leveraged to ensure the success of a spear phishing attack indicates that the criminals are stepping up their game.
 14 DAY TRIAL //
14 DAY TRIAL //