Researchers from ThreatTrack Security have come across an interesting scheme that’s designed to phish out the victim’s Facebook credentials and trick them into installing a Bitcoin miner on their devices.
According to ThreatTrack Security’s Chris Boyd, it all starts with a Facebook post that reads something like this: “I’m serious guys if you people don’t stop posting this of me I will be erasing my account [link].”
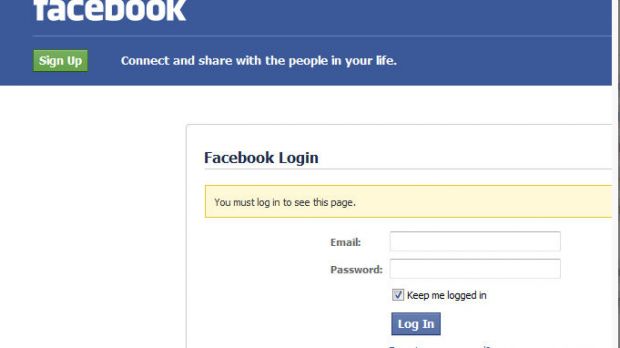
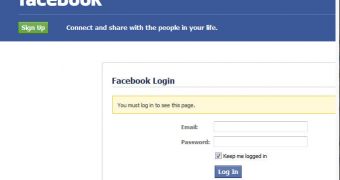
Users who click on the link are taken to a Tumblr page that’s designed to redirect them to a Facebook phishing site.
Once the victim enters his/her email address and password, another page appears asking for the answer to a security question that the user can choose.
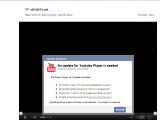
After this part of the scheme is completed, internauts are taken to another page where they’re asked to install a Flash Player update that’s allegedly needed to view a video.
Of course, the file that’s served by the website is not a genuine Flash Player update, but a .vbs file.
Once it’s executed, the victim is informed that the installation has failed and that the computer must be restarted to “prevent any damages.”
In the meantime, the threat installs Java (if it’s not already installed) and starts downloading .JAR files.
“It appears that once they’re done redirecting you to fake Facebook pages, stealing your login / security question information and loading up a fake video page they then want your PC to go mining (most likely Bitcoin, though the files aren’t displaying much activity at time of writing),” Boyd explained in a blog post.
It’s worth noting that the fake Flash Player update page is identical to one used in a spam campaign that was doing the rounds on Twitter in 2012. However, the downloaded file and the cybercriminals’ goals are different.
 14 DAY TRIAL //
14 DAY TRIAL //