Although Apple says there are no Masque attacks reported in the wild, this particular flaw is actually one of the easiest ways to get malware onto an iDevice. Hence, you need to stay on the safe side until the hole gets closed with a software update. Here’s how to do that.
Apple said in a statement issued to the press hours ago, “We're not aware of any customers that have actually been affected by this attack,” but at the same time added that it encouraged customers to “only download from trusted sources like the App Store and to pay attention to any warnings as they download apps.” For Enterprise users, the safest approach is to only get software from their company.
Intriguingly, the company says “trusted sources like the App Store,” but for the regular user, the App Store is the only trusted source of apps. Something that it should make an effort to clarify, considering that 90 percent of the iOS install base is regular folks like you and me.
How to stay safe until the patch arrives
There’s actually no word on whether Apple will deliver a patch. The company’s statement implies that this is basically how iOS works, which could mean that Apple would be required to fundamentally change the system to address the problem.
In any case, until further notice, iOS users can protect themselves from the Masque attack by following these simple steps (not necessarily in tandem).
1. First and foremost, users should not install apps from third-party sources other than iTunes App Store, which is the only official repository of apps for iDevices.
2. Users wielding an iPhone or iPad deployed in their firm via the Device Enrollment Program will also have the option to install apps coming from the company’s server. This is where both the administrator and the user need to ensure that the software about to be installed is indeed coming from the company’s servers, and not an external source.
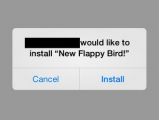
3. This is probably the most important warning for young users who may be tempted to get free games. Whatever you do, don’t click “Install” on a pop-up from a third-party web page (as shown in screenshot #8, courtesy of FireEye). As the flaw’s discoverers noted earlier this week, “The pop-up can show attractive app titles crafted by the attacker.” Again, if it’s not from the App Store, you have every reason to be concerned that it’s malware.
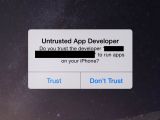
4. If you’re trying to open an app and iOS shows an alert that states “Untrusted App Developer” (again, as shown in the above screenshots, #9 this time) tap “Don’t Trust” and get rid of the app.
FireEye reports, “We disclosed this vulnerability to Apple in July. Because all the existing standard protections or interfaces by Apple cannot prevent such an attack, we are asking Apple to provide more powerful interfaces to professional security vendors to protect enterprise users from these and other advanced attacks.”
Hopefully, Apple will respond with a timely update.
 14 DAY TRIAL //
14 DAY TRIAL //