In a two-month period, a security enthusiast recorded about 8,000 attacks targeting Elasticsearch servers, most of the offending IP addresses being located in China.
The data was collected by Jordan Wright from a honeypot system called Elastichoney, which he built after being notified by virtual private server provider DigitalOcean about the fact that one of the servers he managed was executing a distributed denial-of-service (DDoS) attack on another host.
93% of the offensive IPs are from China
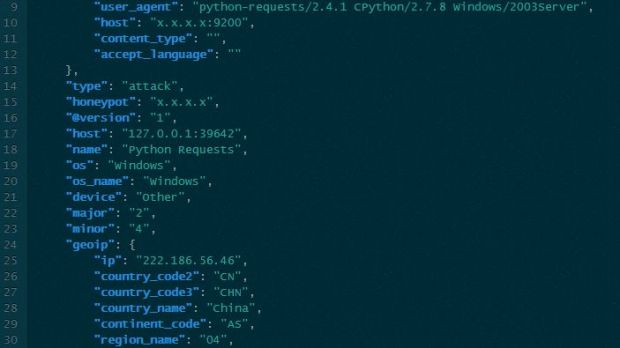
Wright determined that the attackers ran an exploit for CVE-2015-1427, a security flaw affecting Elasticsearch versions earlier than 1.3.8 and 1.4.3 that allows remote code execution (RCE) on a vulnerable machine.
“Elastichoney keeps track of quite a bit of data, including the source IP and payload sent to the sensor. I logged every attack to an Elasticsearch instance (have some irony - free of charge!) and enriched the data with geoip information using Logstash. Finally, I created a slick dashboard using Kibana to view the results,” he said in a blog post on Monday.
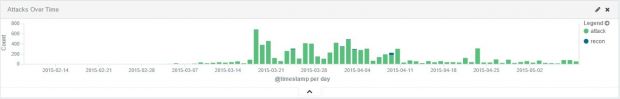
According to the logs, the attacks started in early March and intensified between March 20 and April 11. More than 300 unique IP addresses were used for the assaults, 93% of them being assigned to machines in China.
Wright says that the events from the spike period came from a few Chinese IPs and the attacks halted at the same time. Apparently, the researcher does not have any explanation for the reason behind this.
Patch available since February, exploit code published in March
Some of the attacks seemed to be aimed at identifying the Elasticsearch servers as they would run commands like “whoami,” but in some cases, the “wget” download component was used for funneling in malware samples under the form of ELF binaries or PERL scripts for bots.
Elastichoney does not support automatic downloading of the samples, but the developers behind it are working on introducing this capability. However, all the activity has been captured and Wright makes it available for others to investigate.
The Elasticsearch versions that include a patch for the RCE vulnerability exploited by the attackers were released on February 11, 2015, but some of the administrators have not applied the most recent updates.
Furthermore, proof-of-concept (PoC) code for the flaw was published in March by security consultancy and software development company Xiphos Research.
 14 DAY TRIAL //
14 DAY TRIAL //