A malware sample for Android that integrates a rare suite of malicious functions, such as uploading SMS messages, stealing banking credentials, and sending text, has been discovered to target Korean users.
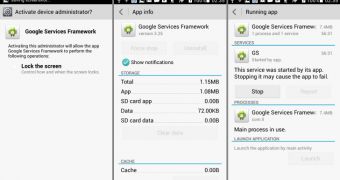
The sample, dubbed HijackRAT, was analyzed by FireEye mobile security researchers, who found that the malicious APK poses as a Google Service Framework.
At the moment, it is aimed at stealing banking info from eight Korean banks, but the researchers say that the list can be further expanded in just half an hour of coding.
Once it is installed on the victim’s mobile device, the malware places a new item on the home screen, under the name Google Services, marked with the default Android icon.
Upon launching it, the malware requests administrative privileges, which, given that it looks legitimate, most users would grant. This makes the process of removing it more difficult because not all users know how to strip an app of elevated privileges from Android’s Settings menu.
A process is then created, named GS, that communicates with the command and control server (C&C) for new instructions.
The researchers have identified the location of the C&C in Hong Kong, but it is unsure if it is under the direct control of the cybercriminals or it is another infected device used for sending the instruction set.
Attempting to relaunch the app generates an error saying “App isn’t installed,” and removes itself from the home screen, thus erasing any visible trace of its presence on the device.
The first malicious action taken by HijackRAT is to upload information about the phone (number and device ID) and the list of contacts available, possibly for duping other victims into infecting their devices.
FireEye says that HijackRAT targets a number of eight Korean banks, whose Android apps are replaced when the cybercriminal issues the update command.
However, it appears that this function does not work too well, “so far the part after the installation of the fake app is not finished yet. We believe the hacker is having some problems finishing the function temporarily.”
The official banking apps require the installation of a particular antivirus software from Google Play. To avoid detection, the malware has the capability to disable the antivirus so that it can manipulate the bank apps.
A similar malware has been reported last week. In both cases, the threat poses as a legitimate app and removes itself on the second launch, after the malicious service has been deployed.
The list of targeted banks provided by FireEye researchers appears to be the same, and both malware replace the legitimate banking app on the victim’s device through an update request.
CheetahMobile did not report the malware having any trouble replacing the official online banking apps.
In any case, if it is the same sample, FireEye gave it a name and published a more extensive analysis of the way it carries out the mischievous activity.
 14 DAY TRIAL //
14 DAY TRIAL //