A new, very elaborate phishing campaign has been spotted to aim at French-speaking computer users, in an attempt to steal their online banking credentials.
The cybercriminals do not rely on direct phishing, which supposes sending a message claiming to be from a financial institution that asks them to sign into the bank services via a provided link.
Instead, the email purports to be from a different entity, which informs that some sort of billing mistake has occurred and money has to be refunded (sometimes as much as €95 / $127) to their account. The user then has to provide information on the bank where the transfer should be made.
This is the actual phishing the campaign’s operators are trying to perpetrate, because the potential victim is then directed to a page that collects the banking details.
The sophisticated nature of the scam is also given by the fact that the credentials to the third party are first verified before allowing the victim to proceed.
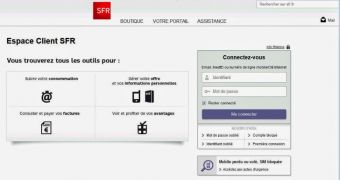
Gary Warner from Malcovery Security detected the new campaign and observed that the third party entity chosen by the crooks is SFR, a French telecommunications company that provides phone services (mobile and landline), along with Internet and IP TV products.
According to the researcher, this campaign is not new, as it has been previously seen in circulation, but it has been re-invented through the SFR login verification process that is being performed.
When the user provides the login credentials on the phishing site, the information is actually passed to SFR and verified if it is real. If the details are not correct, a message is returned informing of the error and that after five failed login attempts the account would be blocked.
This only increases users’ trust that the communication actually comes from the real company, and they feel more confident to provide the true details.
The next step in the scam is for the victim to select from a list of French banks they’re doing business with. There is a wide variety (over 30 institutions) to choose from, and chances are one of them is used by the victim.
“Depending on which bank they choose, they will be prompted for appropriate additional verification details used by that bank,” writes Warner. Through this form, the cybercriminals are basically collecting all the data required to access the bank account.
It appears that after all the info is exfiltrated, the phishing page thanks the user for using the SFR services and redirects them to the legitimate website of the company.
According to the researcher, the popularity of this campaign has increased this year. “Malcovery's PhishIQ service has seen more than 1,000 SFR phish on more than 330 hacked servers so far this year, including dozens just in the month of July 2014.”
As far as the complexity of the scheme is concerned, Warner says that “one of the most sophisticated phish we've seen to date, employing ‘man-in-the-middle’ logins where SFR credentials are tested before the victim is allowed to proceed, and nearly a dozen customized bank security procedure questions being processed.”
 14 DAY TRIAL //
14 DAY TRIAL //