An active email campaign was deployed towards the end of February with the purpose of infecting user machines with CryptoWall ransomware; the messages carry interactive help files (CHM) infected with a malware downloader that delivers the final payload.
CryptoWall has file encryption capabilities and starts locking the data on the computer as soon as it is launched. When the process completes, the user receives a ransom message asking to pay a certain amount of money in digital currency bitcoin, or the information stays encrypted for good.
Campaign delivers the latest version of CryptoWall
The nefarious messages try to trick the recipient into launching a CHM file that claims to be a fax report, suggesting that the cybercriminals target business computers that still rely on electronic fax services for company communication.
Security researchers at Bitdefender have determined that the malicious servers spewing the malicious messages are located in Vietnam, India, Australia, the US, Romania and Spain; but victims have been located in other parts of the world.
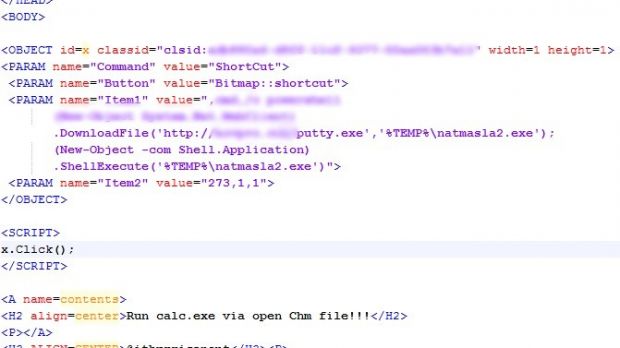
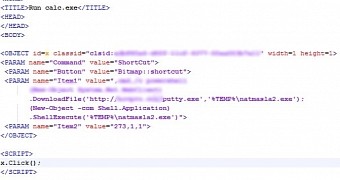
“Once the content of the .chm archive is accessed, the malicious code downloads from this location http://*********/putty.exe, saves itself as %temp%\natmasla2.exe and executes the malware,” researchers say in a blog post on Monday.
The version of CryptoWall delivered this way is 3.0, the latest one spotted in the wild since mid-January, Bitdefender said via email. This means the command and control servers are well hidden in the I2P anonymity network.
Hundreds of infections detected in the first day of the campaign
According to Bitdefender senior threat analyst Bogdan Botezatu, the attackers use two different malware downloaders in the operation, one of them being more widespread than the other.
The latest detection recorded by Bitdefender occurred on Monday, indicating that the spam operation is still ongoing. Researchers noticed the campaign on February 18, when about 300 infections were recorded in the US alone.
As per data from the Romania-based antivirus vendor, the most affected countries are United States, Japan, Australia, Canada, Germany, United Kingdom, and Romania. However, infections have been recorded in the Netherlands, Denmark, Sweden and Slovakia, too.
CHM files are included with software programs to provide instructions on how the product functions and present the different features available.
They consist of compressed HTML files, images and JavaScript content. One functionality in CHM is that it can redirect to external web addresses automatically after they are executed.
One of the best ways to avoid damage in the wake of being infected with ransomware that can encrypt files is to maintain an updated backup file on an isolated system or storage drive with restricted access. Preventing an infection can be achieved by running an up-to-date reputable antivirus product on the computer and refraining from opening files and messages from unknown or suspicious sources.
 14 DAY TRIAL //
14 DAY TRIAL //