Trend Micro has released a paper which focuses on an active advanced persistent threat (APT) dubbed HeartBeat, a cybercriminal campaign that targets the South Korean government and some related organizations since at least 2009.
According to researchers, the HearBeat campaign mainly targets South Korean political parties, branches of the government, media outfits, a military branch of the armed forces, a small business sector organization and a national policy research institute.
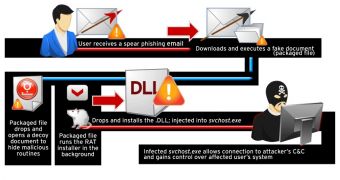
The first component of the remote administration tool (RAT) used in this operation was discovered in June 2012 in the networks of a Korean newspaper. After further investigations, experts learned that the RAT had been used in 2011 as well and the earliest component of the malware dated to November 2009.
The cybercriminals are spreading the RAT by disguising it as a harmless document. When executed, a legitimate document is opened to avoid raising any suspicion, but in the background the malicious element steps into play.
For the time being it’s uncertain how the documents are distributed, but experts believe that spearphishing emails might be utilized.
Once it makes itself cozy on a computer, the RAT drops a component that has backdoor capabilities, allowing its mastermind to remotely execute various commands on the affected system.
Because they deploy some clever techniques to hide their tracks, including the use of compromised hosts as command and control (C&C) proxy servers, it’s difficult to identify the perpetrators.
While in some cases the code contains Chinese words, some of the C&C domain names contain English words. Furthermore, the binder tool and the RAT component are both written in English.
The campaign has been named HeartBeat because the malicious code contains this particular piece of text.
The complete paper on HeartBeat is available here.
 14 DAY TRIAL //
14 DAY TRIAL //