New infections with Havex remote access Trojan (RAT) have been discovered by security researchers, who observed that malware authors attempt to bypass detection by signing the threat themselves.
The files with the spoofed digital signature attempt to pass as components created by IBM’s software division.
Researchers from Trend Micro also found the first version of the malware designed to compromise 64-bit systems.
Newly found 64-bit version pre-dates 32-bit ones
Havex RAT has been created for the purpose of stealing data from targets in different activity sectors such as industrial (ICS/SCADA), manufacturing, pharmaceutical, construction or education.
It is part of an active cyber-espionage campaign that has been discovered at the beginning of 2014, but which has been traced as far back as 2010. The operation is also known under the names of Energetic Bear and Crouching Yeti.
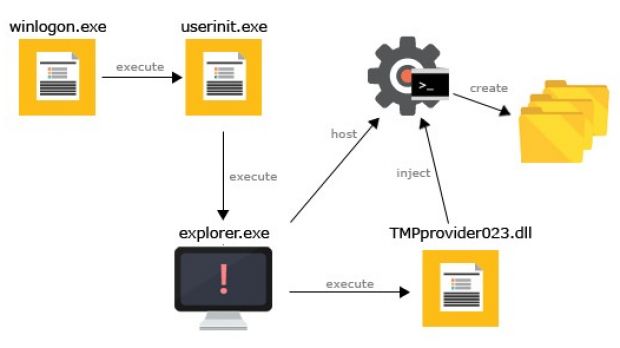
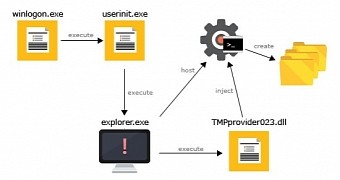
Up until recently, only 32-bit samples of the malware have been discovered, but Jay Yaneza of Trend Micro reported that a 64-bit version (TMPprovider023.dll, where the number indicates the version of the malware) was discovered with a compilation date of October 3, 2012, which is older than the newer versions analyzed by the researchers.
According to Trend Micro analysis, TMPpovider023.dll creates two files in the file system and it is in charge of communicating with the command and control servers to receive instructions such as downloading additional modules or executing commands.
It appears that from the 64-bit version of the malware (v023), a 32-bit one emerged, with the name TMPprovider029.dll.
Based on the analysis, the researchers were able to determine another three files “that seem to be interrelated in one single infection:” 34CD.tmp.dll, 734.tmp.dll and 4F2.tmp.dll; all of them were compiled starting the second quarter of 2013.
Self-signing was obvious
In a different infection, Trend Micro discovered components that seemed to be signed by IBM, “despite being obvious that the digital certificate was self-signed.”
“Properly signed files should come with a trusted certificate authority to validate the issued digital certificate, but these files had none. While we are unable to determine which software package had these files at this point in time, what’s interesting is that there are three other files that bear a similar digital signature as the one seen above. All these files are detected as BKDR_HAVEX.SM,” Yaneza says in a blog post published on Monday.
The researcher stresses the fact that Havex has already been modified plenty of times to evade detection and that its operators will continue to do so in order to evade the new detection capabilities of security solutions.
 14 DAY TRIAL //
14 DAY TRIAL //