Last week, hackers breached and defaced the blog of Mark Karpeles, the CEO of the Bitcoin exchange Mt. Gox. They claimed to have exposed Karpeles’ lies about hundreds of thousands of customer Bitcoins being stolen. However, experts say the attackers had a different agenda.
The hackers published a post on the CEO’s blog with a link to a 716 Mb archive file. They also posted balances for various currencies, apparently showing that Mt. Gox still had over 950,000 Bitcoins.
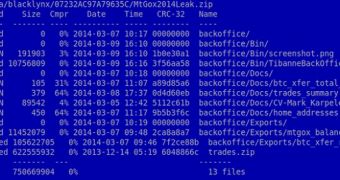
The archive file contained some Bitcoin transactions, a CV of Karpeles, a screenshot apparently showing the exchanges databases and some software.
Experts from Kaspersky have analyzed the leaked data and have determined that most of it has been publicly available. The software contained in the archive is actually the most interesting.
One of the applications is a Trojan detected by Kaspersky as Trojan.Win32.CoinStealer.i. This is a piece of malware that’s designed to steal Bitcoin wallet files from infected computers.
The Trojan has been developed in Livecode, a programming language that can be used to create apps for multiple platforms. The cybercriminals have planted binaries for both Windows and Mac computers in the archive linked from the defaced blog.
When victims execute the application, they see what appears to be a program for accessing the databases of Tibanne Co. Ltd, the company that operates Mt. Gox. In the meantime, their Bitcoins are being stolen.
“The Livecode application contains the source code as an encrypted and packed binary that’s available when executed,” Kaspersky’s Sergey Lozhkin explained in a blog post.
“The malware creates and executes the TibanneSocket.exe binary and searches for the filesbitcoin.conf and wallet.dat – the latter is a critical data file for a Bitcoin crypto-currency user: if it is kept unencrypted and is stolen, cybercriminals will gain access to all Bitcoins the user has in his possession for that specific account,” Lozhkin added.
The stolen information was sent to a remote server that was located on Bulgaria. In the meantime, the server has been shut down.
This is a perfect attack scenario. The hackers know that a lot of Mt. Gox customers are anxious to find out what happened to their Bitcoins, so they deface the company’s CEO’s blog and make fraud accusations.
Of course, customers will be curious to see “the evidence,” so they download the files. Since most of the people who downloaded and executed the files owned Bitcoins, the malware probably stole a lot of wallets.
For additional technical details on the Bitcoin-stealing malware, check out Kaspersky’s Securelist blog.
 14 DAY TRIAL //
14 DAY TRIAL //