It turns out that during the period in which everyone was talking about Hurricane Sandy, cybercriminals didn’t target just regular internauts by leveraging the topic, but also high-profile organizations.
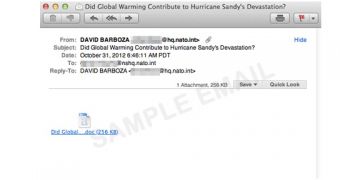
On October 31, a Hurricane Sandy-themed email landed in the inbox of a NATO Special Operations Headquarters (NSHQ) staffer, Trend Micro reports.
The malicious notification contained a Word document entitled “Did Global Warming Contribute to Hurricane Sandy’s Devastation.” The cleverly crafted document was actually set up to exploit an RTF stack buffer overflow vulnerability in order to drop a backdoor detected as BKDR_DLDR.A.
Although this particular vulnerability was patched by Microsoft precisely two years ago, cybercriminals are still exploiting it in their campaigns.
The malware in question, BKDR_DLDR.A., allows its master to perform various operations, including downloading, modifying, copying, and creating files. It can also be used successfully for information theft.
It’s uncertain if this attack is part of a larger operation and it’s uncertain what the attackers were after. NATO and NSHQ have been alerted about the incident.
 14 DAY TRIAL //
14 DAY TRIAL //