Researchers continue to analyze the recent cyberattack against the systems of US retailer Target. Experts from Seculert have published a blog post in which they provide some interesting details about the attack.
Seculert has found that the attack had two stages. In the first one, it infected point-of-sale (POS) registers from which payment card and other personal information was stolen.
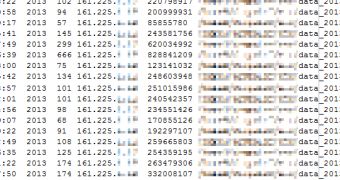
The second phase began 6 days later, on December 2, when the malware started sending the harvested data to an external FTP server hosted on a hijacked website. Another compromised server from within Target’s network was used to transfer the information.
On December 2, the attackers started downloading the loot from this FTP server using a virtual private server (VPS) located in Russia. Over a period of two weeks, a total of 11 Gb of sensitive information was transferred.
The cybercriminals didn’t retrieve all the data at once. The data transmissions took place several times a day during the two-week period.
“While none of this data remains on the FTP server today, analysis of publicly available access logs indicates that Target was the only retailer affected. So far there is no indication of any relationship to the Neiman Marcus attack,” Aviv Raff, CTO of Seculert, noted.
Earlier this week, Brian Krebs revealed that the malware used in the attack was most likely BlackPOS, a threat apparently developed by a group of Russians and Ukrainians.
Raff has told Softpedia that the malware they’ve analyzed appears to be similar to BlackPOS, probably derived from it, but with additional components.
As far as the Neiman Marcus breach is concerned, few details have been provided by the company. Unlike Target, the high-end retailer hasn’t revealed how many people are impacted by the incident.
 14 DAY TRIAL //
14 DAY TRIAL //