Bitdefender warns users that cybercriminals are trying to hijack their accounts by relying on a cross-site scripting (XSS) type of attack.
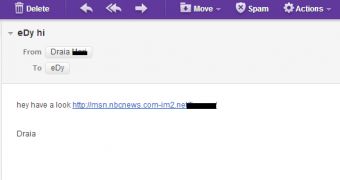
It all starts with an email coming from a contact. The message doesn’t say much, except for “check out this page,” followed by a link.
The link appears to lead to a legitimate MSNBC news page. However, a closer look at the link, www.msnbc.msn.com-im9.net, reveals that MSNBC is just a subdomain of com-im9.net, a domain registered in Ukraine earlier this month.
The webpage users are taken to contains a malicious JavaScript disguised as a Lightbox library. This JavaScript exploits a vulnerability in the Yahoo! Developers Blog (developers.yahoo.com) in order to steal the victim’s authentication cookies and use them to gain access to the email account.
This is possible because the Developers Blog utilizes a flawed version of WordPress which contains the CVE-2012-3414 vulnerability. WordPress has patched this particular security hole with version 3.3.2, but Yahoo! hasn’t updated its blog.
Once they gain access to the accounts, cybercriminals can steal contacts and use the harvested addresses to send out spam emails or malware. They don’t even need too much time to perform their malicious activities.
As Bitdefender experts highlight, it’s much more efficient for cybercriminals to hijack active accounts and utilize them for spam than it is to register new accounts. That’s because most email service providers still use decent CAPTCHAs for the account registration process.
To avoid falling victim to such attacks, experts advise users to log out of their email accounts once they’re done checking or writing messages. Secondly, always keep an up-to-date antivirus application running in the background since in many cases it will keep you out of harm’s way.
Finally, the old rule: never click on suspicious looking links, even if they appear to come from someone you trust.
 14 DAY TRIAL //
14 DAY TRIAL //