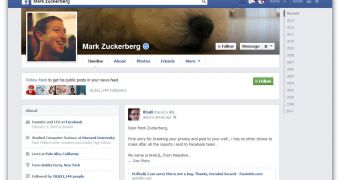
When Khalil Shreateh reported a security bug to Facebook via the regular channels, his reports were ignored as Facebook engineers weren't able to replicate the bug. So he found another way to get attention, by using the very bug he was trying to report to post a link with the details of the bug on Facebook Founder Mark Zuckerberg's wall.
The vulnerability enabled anyone to post a link on any Facebook user's wall, even if they didn't have them in their friends list.
Shreateh first tested the bug on the profile of Sarah Goodin, a friend of Zuckerberg's and the first woman to join the site. But since the post was only visible to friends, a security engineer at the company wasn't able to verify the report. "This is not a bug," he replied.
So the next step was to try out the bug on Zuckerberg's wall, where it certainly got attention, an engineer contacted Shreateh within minutes. His account was also disabled, but was later restored.
Normally, a bug as serious as this would be eligible for a $500 (€375) reward, but Facebook says the researcher violated the Whitehat's program terms of service, using the bug to affect the profiles of regular users, so Shreateh won't be getting anything.
"The more important issue here is with how the bug was demonstrated using the accounts of real people without their permission. Exploiting bugs to impact real users is not acceptable behavior for a white hat. We allow researchers to create test accounts [...] to help facilitate responsible research and testing," a Facebook engineer wrote on Hacker News.
He has also explained that Facebook gets hundreds of security reports each day, many of them in bad English and many of them not being a bug at all.
Still, many who joined the discussion on Hacker News believed Shreateh should be paid, regardless of the way he reported the bug, especially since his first attempts were ignored.
 14 DAY TRIAL //
14 DAY TRIAL //