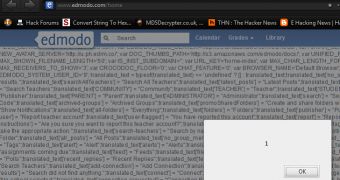
The popular e-learning platform Edmodo (edmodo.com), used by 6.6 million teachers and students worldwide, contains a number of vulnerabilities that could be leveraged by hackers to cause some serious damage to unsuspecting internauts. The hacker known as Gambit provided us with information that demonstrates the existence of a persistent cross-site scripting (XSS) vulnerability and a cross-site request forgery (CSRF) flaw that affect Edmodo.
“Well, I contacted the admins a few weeks ago and they thanked me for reporting the vulnerabilities (persistent XSS and later a CSRF through the same vulnerable spot.),” Gambit explained.
“After reporting the CRSF a day or so later, he again thanked me and said he passed both the vulnerabilities up to one of the lead engineers. Well, weeks go by like I said and here we are, still not fixed.”
The existence of these weaknesses shouldn’t be treated lightly because many of the site’s users, especially the younger ones, know nothing about online security and best practices and they can easily become victims when presented with a malicious webpage.
Sites that are being used by millions of people worldwide can always be tempting for cybercriminals who want to launch phishing attacks and other operations that one way or the other help them earn money.
This is why it’s important for the owners of such websites to ensure that the common SQL Injection and XSS vulnerabilities are addressed. Furthermore, when persistent XSS and CSRF security holes are involved, the threat level for the site’s customers increases.
In the past we’ve seen that hackers and website owners can collaborate well.
However, recent events have shown that white hats and grey hats are more than willing to offer their services, the bigger issue being with administrators and website owners who either see the hackers as a threat, or simply don’t know what to do with the information they are presented with.
Note. My Twitter account has been erroneously suspended. While this is sorted out, you can contact me via my author profile or follow me at @EduardKovacs1
 14 DAY TRIAL //
14 DAY TRIAL //