The fingerprint of German Defense Minister Ursula von der Leyen has been obtained by a hacker by simply scanning her thumb in photos that have been made public by media outlets.
With enough care, fingerprints can be copied from objects with polished surfaces that have been touched by an individual. This method is also used by the police, but security researchers have already demonstrated that it can be done by anyone.
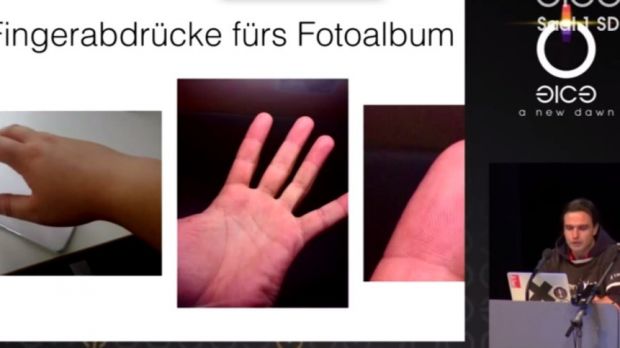
Fingerprints can be recreated from images
At the Chaos Computer Club hacker conference in Hamburg this year, Jan Krissler, also known as Starbug, held a presentation (see below, in German) explaining how the biometric feature can be reproduced from photos of a finger.
Krissler is a security researcher at Technical University of Berlin, looking into the weaknesses of the biometric security systems.
He managed to pull this off relying on a photo of von der Leyen’s thumb, taken at a news conference in October. Additional close-range photographs were used to fill in the missing parts of the fingerprint.
The tool used by the researcher was VeriFinger, which integrates fingerprint identification technology. The software is designed for biometric system integrators and it relies on a powerful algorithm that complies with the standard fingerprint identification scheme.
VeriFinger’s features include high accuracy for matching rolled and flat fingerprints, detection of the fingerprint even if it is rotated, deformed, or has only 5-7 similar minutiae (major characteristics of a fingerprint – generally, there are between 20 and 40 such similar features in a fingerprint of the same finger).
During the presentation, Krissler explained the importance of this tolerance in fingerprint identification software.
The Fingerprint Extractor component of the application is available for consumers and comes for a price of €20 / $24.40 if up to nine licenses are purchased.
Fingerprint identification has increased in popularity
Obtaining a fingerprint through Krissler’s method, bypassing biometric systems integrated for securing access to different assets becomes much easier because physical access to objects touched by the target is no longer required.
Given that high performance cameras can be purchased by consumers, and biometric protection systems have already been integrated in mobile devices such as smartphones, thieves now have increased chances of getting the information they’re after; of course, this is valid in the case of targeted attacks.
Some users rely on fingerprint recognition to unlock their computers, but devices accomplishing this feat are also available in airports, government buildings, and law enforcement agencies.
Not only fingerprints are used for identity verification, and iris scans are also employed. Krissler’s presentation touched on facial recognition software as well, demonstrating how a good quality photo can fool such technology.

 14 DAY TRIAL //
14 DAY TRIAL //