Gourab Paul, a cyber-security enthusiast, claims to have identified a number of serious security holes in the websites designed by TechShot Digital for a number of professional cricket players from India. He accuses the company of neglecting to properly secure the sites.
“As we know our India is very much passionate about CRICKET, and those who play the game are very much popular. Our Indian proud captain MS Dhoni and some other players have their official websites made by TechShot Digital (TSD),” he wrote next to the details of the vulnerabilities he identified.
“It’s OK up to that, but TSD made the websites of the Indian cricketers without having core knowledge of web designing. They made the official websites of these players with plenty of errors and poor coding, and they can be hacked by a beginner level hacker,” he added.
He told Softpedia that he initially wanted to report these vulnerabilities to the company, but he later decided to make them public to let the players know that their personal websites are not secure.
“I just want to convey my message and TSD's faults to the Indian Cricket players. Because there are many companies like these who will charge money from you in the name of technology and will make you fools by delivering poor service,” he said.
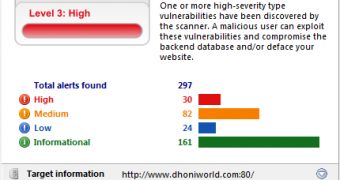
To demonstrate his findings, the expert has published the details of a number of vulnerabilities present on the site of famous cricket player MS Dhoni. The security holes include a number of cross-site scripting (XSS) flaws and a “file upload vulnerability.”
He claims that the issues he identified can be utilized by an attacker to cause some serious damage.
“Any one can easily upload php files, image shells and deface pages as well. One of the directories may expose sensitive information that could help a malicious user to prepare more advanced attacks,” he explained.
We have attempted to contact TSD representatives to give them the chance to respond to these accusations, but so far we haven’t heard back from them.
Note. We will not provide the link to the proof-of-concepts published by Gourab, but we have been able to reproduce some of the vulnerabilities he uncovered.
 14 DAY TRIAL //
14 DAY TRIAL //