Email-based attacks luring UK citizens to a fraudulent HM Revenue and Customs (HMRC) web page rely on an image hosted on the systems of a web security company that is now part of Trustwave’s SpiderLabs.
The entire malicious message is a PNG photo retrieved from a 2010 article from M86 Security Labs, which, ironically, warned of HMRC phishing attacks.
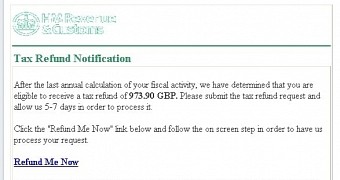
Fake message pulled from security firm's server
The media item was loaded in the message straight from M86’s server. The text shown in the interactive picture informed the recipient that they were eligible to receive a tax refund of ₤974 / $1,460 / €1,374.
The amount of money is enough of an incentive to pique the interest of the user and seek for more details. Clicking anywhere in the image would take them to a risky website controlled by the cybercriminals.
According to Paul Mutton from UK-based web security company Netcraft, the phishing site is hosted in Turkey and has been set up to collect the victims’ full names, email addresses, dates of birth, postal addresses and payment card details.
Tax refund is a popular phishing theme
In most cases, the request to provide card data may not raise any suspicion since the fraudulent message alerted the recipient that this type of information would be needed in order to transfer the money.
To make sure that the correct details are entered by the victim, the crooks also say that one of the reasons for delaying the refund is providing invalid records.
“Fake HMRC tax refunds remain a popular ruse,” the researcher said in a blog post on Wednesday.
He also added that in February Netcraft blocked a total of 1,150 phishing websites that impersonated HMRC’s page.
At the moment of writing, the image used by the cybercriminals in the phishing campaign is no longer available in M86’s article. The security researchers updated the blog post on Wednesday simply saying that the image file was removed.
By doing so, the researchers render the entire phishing campaign useless as the fake content is no longer loaded in the emails.
 14 DAY TRIAL //
14 DAY TRIAL //