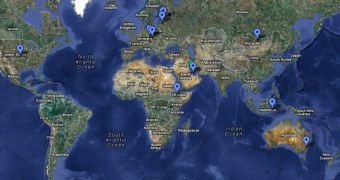
FinFisher, an infamous cyberweapon, known for its advanced capabilities when it comes to remotely monitoring computers, has been found to have command and control (C&C) servers in ten different countries all around the world.
The lawful interception tool – developed by Gamma International UK Ltd. – is renowned because it’s currently utilized by many governments to spy on its citizens. FinFisher is able to harvest dumped data, logs and screenshots, all of which it sends back to its control servers.
While there has been a lot of controversy regarding the fact that the software may actually be in the possession of other actors besides governments – even WikiLeaks published some files – no one actually got to analyze it, at least until now.
At the end of July, Bloomberg journalists obtained a copy of FinFisher that had been used in attacks against Bahrain activists.
The files have been handed over to researchers from Citizen Lab who performed a detailed analysis on it.
Now, security experts from Rapid 7 have made their own analysis and found that command and control servers used by FinFisher are scattered all around the world in countries such as: Indonesia, Australia, Qatar, Ethiopia, Czech Republic, Estonia, USA, Mongolia, Latvia and the United Arab Emirates.
Claudio Guarnieri of Rapid 7 highlights the fact that these results have been obtained based on fingerprinting and that they can’t be utilized to determine if the servers are controlled by governments or by “local people.”
“The malware seems fairly complex and well protected/ obfuscated, but the infection chain is pretty weak and unsophisticated. The ability to fingerprint the C&C was frankly embarrassing, particularly for malware like this. Combined, these factors really don’t support the suggestion that thieves refactored the malware for black market use,” Guarnieri explained.
However, the important thing is that some samples have been identified, and security solutions providers can make sure that their products can detect the spyware and mitigate the threats it poses.
 14 DAY TRIAL //
14 DAY TRIAL //