Malware has been specifically crafted for the systems used by the employees at the Vietnamese Ministry of Natural Resources and Environment (MONRE).
Phishing campaigns do not always have clear victims, but in this case it looks that the perpetrators are after government data and have created malicious software that can circumvent the protection on the agency’s machines.
The attack begins with an email with an infected Microsoft Word document in the attachment, which, once opened, drops an executable file on the computer, called “payload.exe;“ this is the Trojan dropper that downloads additional executable files.
Oh Sieng Chye from ESET says that the ministry relies on a webmail solution for exchanging email messages, which means that the corrupted file has to be downloaded on the computer for the infection to happen.
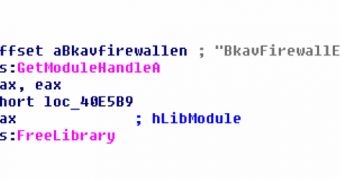
Evidence that the attack is targeted and may be supported by organizations of a different government lies in the fact that the threat performs a scan to check for the presence of the BKAV (Bach Khoa Anti-Virus), a Vietnamese security tool.
The malware contacts a remote location for receiving new files and commands, and the researchers determined that it communicates with two servers, one in the US (31.170.167.168) and one in South Korea (www.google.zzux.com). In both cases port 443 is used, which indicates that the traffic is encrypted.
Sieng Chye notes that “a connection to the zzux.com domain was tried only if the IP address for the host is different from the IP address 31.170.167.168.”
The communication is initiated by “Framework.dll,” a backdoor that delivers the local IP address of the infected machine and opens a Windows command shell that redirects the input and the output to the command and control server.
If the antivirus is detected, the Trojan dropper unloads “BkavFirewallEngine.dll” from memory using the FreeLibrary functions, thus bypassing its protection.
The three items added by the dropper on the system are stored in a temporary directory and, according to ESET, they are quite recent, as the date in the PE header indicates April 24, 2014.
All the files downloaded on the system are currently detected by ESET products as Win32/Agent.VXU.
The Ministry of Natural Resources and Environment may seem like an odd target for an attack, but it is still a government agency that can handle sensitive information. Furthermore, among the details extracted from the compromised systems there can be information that could prove useful in launching similar attacks on other structures of the government.
 14 DAY TRIAL //
14 DAY TRIAL //