On Sunday, BGPmon, a network monitoring and routing security company that monitors the Internet for Border Gateway Protocol (BGP) attacks, revealed that Google’s public DNS service had been hijacked.
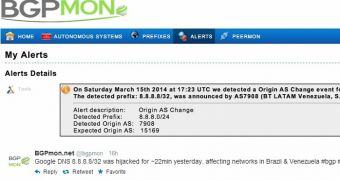
The attackers hijacked the 8.8.8.8/32 DNS server for approximately 22 minutes. According to BGPmon, networks in Brazil and Venezuela were impacted. A screenshot published by the company shows that the traffic was redirected to BT Latin America’s networks.
BGPmon has noted that the potential for misuse in the case of such hijackings is “huge,” especially since many certificate authorities don’t do their job as well as they should.
Google Public DNS was introduced back in December 2009 in an effort to make the web faster and more secure. Last year in March, the search engine giant made some improvements to the resolver, adding support for Domain Name System Security Extensions (DNSSEC) validation.
The security feature is designed to protect users against DNS-based attacks and it makes DNS more secure overall. However, as IT News’ Juha Saarinen highlights, there doesn’t appear to be any mechanism in place to protect users against BGP hijacking.
Around 70 million IP addresses use Google’s public DNS servers for 130-150 billion queries every day.
For the time being, it’s uncertain who is behind the attack or how this could have happened. I’ll update the post if more details become available.
Google DNS 8.8.8.8/32 was hijacked for ~22min yesterday, affecting networks in Brazil & Venezuela #bgp #hijack #dns pic.twitter.com/wlBuui8dwO
— BGPmon.net (@bgpmon) March 16, 2014
 14 DAY TRIAL //
14 DAY TRIAL //