Google has been rather pushy when it comes to encrypted connections. It was the first major site to use HTTPS by default, for Gmail, and has recently made HTTPS connections default for Google Search in some cases.
The company is now announcing that it's deploying a new encryption technology and a new method for encrypting connections which it dubs "forward secrecy."
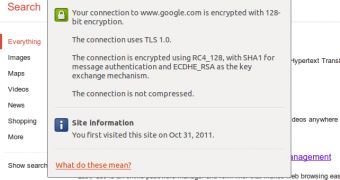
The essence of it is, Google now uses unique keys for each session so even if an attacker would be able to discover the key it would only be good for the traffic from that session.
"Forward secrecy requires that the private keys for a connection are not kept in persistent storage," Google's Adam Langley from the security team wrote.
"An adversary that breaks a single key will no longer be able to decrypt months’ worth of connections; in fact, not even the server operator will be able to retroactively decrypt HTTPS sessions," he explained.
Most major sites today use the same keys to encrypt connections for users for all sessions. This means that all encrypted traffic coming from the same browser can be decrypted if the key is discovered.
While good encryption methods today are considered unbreakable, that may no longer be the case ten years from now.
With Google's new method, all an attacker would be able to get is the data transmitted in a single session.
Google is now using the new method for Gmail, Google Search, Docs and most of its other sites that require or can use an encrypted connection. Google is also open-sourcing its work in the hope that other sites will adopt the solution as well.
However, it is enabled by default only if you're using Google Chrome or Firefox. It works with Internet Explorer running on Vista or Windows 7, but it is not enabled by default since IE doesn't support ECDHE and RC4 at the same time.
 14 DAY TRIAL //
14 DAY TRIAL //