This month's Patch Tuesday rollout includes a total of 14 security updates for Microsoft software, among which a separate bulletin supposed to fix a critical security flaw affecting all versions of Internet Explorer.
MS15-018, flagged as "critical," is described as a cumulative security update for Internet Explorer, which brings a number of fixes for absolutely all versions of the browser, starting with IE6 and ending with IE11.
It also includes a patch for a cross-site scripting security flaw that was first reported in February but wasn’t part of last month's Patch Tuesday release, so Microsoft decided that it wasn't critical enough to launch an out-of-band update and instead preferred to wait until this month.
But what's interesting about this update is that Microsoft worked together with security engineers from Google to address the Internet Explorer flaws.
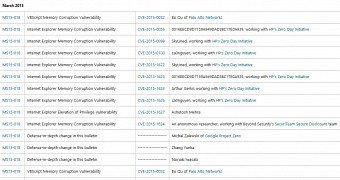
In the Acknowledgments page for March 2015, Microsoft reveals that it worked with several security researchers enrolled in HP's Zero Day Initiative, but also with Michael Zalewski of Google Project Zero for "defense-in-depth change in this bulletin."
Google also helped develop other fixes
The controversy around Google's Project Zero, which a few months ago led to the disclosure of an unpatched critical flaw in Windows, doesn't seem to affect Microsoft's collaboration with security engineers working for the Mountain View-based rival.
Several other Google experts worked with Microsoft to develop patches that were released as part of this month's security update rollout, including Mateusz Jurczyk of Google Project Zero (who contributed to patching the Adobe Font Driver Remote Code Execution Vulnerability) and Ben Hawkes of the Google Security Team (who helped fix a Microsoft Office Memory Corruption Vulnerability).
All these security updates are delivered to Windows systems via the built-in Windows Update, and up until now, there are no reports of botched patches that could break down systems or specific features.
All Windows versions received patches today, including Vista, 7, 8, 8.1, and 10, with the last getting a total of 4 security updates that were only shipped to build TP build 9926.
 14 DAY TRIAL //
14 DAY TRIAL //