Google has rewarded security researchers from Detectify with $10,000 (€7,200) for identifying an XML External Entity (XXE) vulnerability in one of the search engine’s features.
According to experts, the vulnerability plagued the Google Toolbar Button Gallery. Researchers found the security hole after noticing that Google allowed users to customize their toolbars with new buttons. Developers can add their own buttons by uploading XML files containing metadata for styling and other properties.
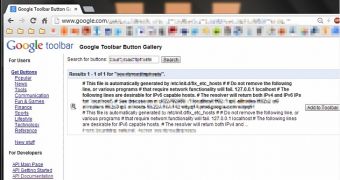
“Fredrik [one of the researchers] read through the API specifications, and crafted his own button containing fishy XML entities. The plan was to conduct an XXE attack as he noticed the title and description fields were printed out when searching for the buttons,” the experts noted in a blog post covering the issue.
“The root cause of XXE vulnerabilities are naive XML parsers that blindly interpret the DTD of the user supplied XML documents. By doing so, you risk having your parser doing a bunch of nasty things. Some issues include: local file access, SSRF and remote file includes, Denial of Service and possible remote code execution.”
The proof of concept they developed shows that they could gain access to /etc/passwd and the /etc/hosts data on one of the company’s production servers. Experts believe they could have accessed any other file on the server and even gained access to internal systems through SSRF exploitation.
Google’s security team responded to Detectify’s report within 20 minutes after being notified. The XXE vulnerability was fixed after a few days.
For additional details on this XXE vulnerability in Google Toolbar Button Gallery check out Detectify’s blog.
 14 DAY TRIAL //
14 DAY TRIAL //