Security researchers warn that a scareware distribution campaign that started before the winter holidays on Google Groups is still affecting users. Rogue shortened URLs redirect unwary visitors to websites aggressively pushing fake antivirus software.
It seems that the scareware cyber-criminal business model is as profitable in 2010 as it was in 2009. One particular distribution campaign targets Google Groups users, who are enticed into visiting tens of thousands of links to fake online videos.
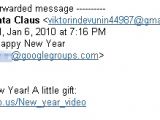
"The users sending out the spam messages all use free Gmail accounts (one even named his spam account Santa Claus), and have been requesting access to both open-membership and closed-membership Groups, the latter of which require an administrator’s approval. Once added to a group’s member list, the spam accounts post brief messages [...] with a link," Andrew Brandt, a threat expert with antivirus vendor Webroot, warns.
The rogue links are generated using various URL shortening services such as tmsurl.com, shrtb.us or cprn.me. Spammers prefer these services over more established ones like bit.ly or TinyURL, because their submissions are not subject to advanced checks for spam or other threats.
When visiting such a link, the user is taken through several silent redirects until reaching the final landing page. First, all links redirect to unique accounts hosted at 150m.com, a legit free Web hosting provider. From there the requests are redirected through various Chinese servers to the final website displaying an embedded video-like image, with ratings and everything. "The shortlinks and Chinese websites only remain viable for a day or two, at most," Mr. Brandt notes.
Regardless of the browser used, the landing page will load a pop-up masquerading as an ActiveX control and asking the visitor to download an executable file. This is in fact the installer for a malicious application from the Antivirus 2009 family of scareware. Called Personal Security, it is able to bombard users with bogus warnings about fictitious infections in English, German and French.
One interesting aspect is that in this instance, all spammers use Gmail email addresses. "If you haven’t signed up for a Gmail account recently, you might not realize that Google has instituted a policy requiring new users to provide a mobile phone number where the company texts a code needed to activate the account. Why hasn’t anyone tracked the malicious activity back to the owner of the phone(s) used to create those accounts?" asks the Webroot researcher.

 14 DAY TRIAL //
14 DAY TRIAL //