A security flaw with the Google Developers website allowed an attacker to trick users into deleting digital assets related to their Google accounts or to retrieve email threads and attachments.
Security researcher Paulos Yibelo discovered that the malicious activity was possible because Google Developers (developers.google.com) did not benefit from a content security policy that allowed its pages to be rendered on other websites in iframes masking the nefarious action, in a type of attack called clickjacking.
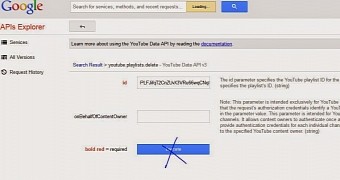
The website is particularly important because it provides access to APIs (application program interface) that can interact with different Google services and make modifications.
A simple trick could cause plenty of damage
Yibelo says that, in lack of clickjacking defenses, such as X-Frame-Options HTTP response headers, an individual had the possibility of completing any action carried out by Google API; this includes removing YouTube playlists, blogs, comments or posts, getting email and attachments, as well as retrieving a user’s activity on Google Plus and the list of friends.
To prove his claims, the researcher made available the requirements and the steps an attacker needed to take to delete someone’s YouTube playlist.
On the list of prerequisites for a successful attack there are previous authorization of the Google API, the ID of the targeted playlist (which is public), and duping the victim into accessing the website where the clickjacking trap is set up.
One method to pull the trick is to “frame that domain, make it transparent and put a clickable button to ‘Execute’ with buttons like ‘Click here to win free iPhone,’” says Yibelo.
Google offers vulnerability reward
For the discovery of this attack method on Google resources, the researcher received a monetary reward of $1,337 / €1,200. The disclosure occurred on April 12, and about a week later, X-Frame-Options protection was added, preventing rendering of the page in a frame, hidden or not, on a different website.
Google dealt with another clickjacking attack at the beginning of April, when it launched a search page that was displayed backwards, for April Fools’ Day.
It turned out that this endeavor also caused the X-Frame-Options in the regular page to be removed, allowing the search settings page to be included in an iframe on a third-party website. The consequence was that an attacker could make a persistent change in the search settings of the victim.
 14 DAY TRIAL //
14 DAY TRIAL //