Along with fixing the insecure use of two WordPress functions popular with plugin developers, Yoast also eliminated in its Google Analytics a stored cross-site scripting (XSS) vulnerability that benefited from much less publicity.
On Monday, Yoast and Sucuri announced a coordinated security release for dozens of WordPress third-party components that would repair a problem with the “add_query_arg()” and “remove_query_arg(),” functions not escaping user input, which could lead to XSS attacks.
Plugin update is critical
Both the SEO and Google Analytics plugins from Yoast were affected and received updates, although the developer said that the issue was not on the frontend, thus representing a smaller risk, and decided not to push the fix via an automatic update, since this procedure created trouble in the past.
However, Jouko Pynnönen of Finish vulnerability research firm Klikki Oy draws attention to the fact that Yoast’s update for Google Analytics (with over 1 million active installations) is of critical security importance due to integration of the stored XSS patch.
Based on Yoast’s assertion that the update for the blog tracking component addresses a minor issue, many website admins may have chosen to install the new version at a later time.
Pynnönen said that the “add_query_arg()” function was present only in one place in the code of Google Analytics by Yoast. “It's a promo box shown to administrators if the WordPress is NOT the English (default) version. So it's not exploitable on English WordPress,” he told us via email.
Critical stored XSS exploitation
He described how the stored XSS attack can be run for server-side execution against websites with a version of the plugin that does not include the security patch (5.3.3 and lower).
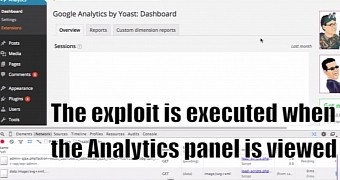
HTML parameters in a page’s URL are not escaped and can be used to point to malicious JavaScript, Pynnönen explains. This way, an authenticated attacker can craft an URL and load it sufficient times to make it in the list of popular pages displayed in the analytics section of the WordPress dashboard.
As soon as the admin checks the analytics panel, the malicious JavaScript is executed and the payload can be dropped on the server, which could lead to total compromise of the website.
“The attacker can perform administrative actions on the target system. By default, this would lead to arbitrary server-side code execution via the plugin or theme editors,” or they could create new admin accounts, a blog post from Klikki Oy informs.
Administrators of websites running Google Analytics by Yoast should update at least to version 5.4 of the plugin to eliminate this risk. The latest build of the component is 5.4.2, available since April 21.
The company created a video demonstrating the flaw:
 14 DAY TRIAL //
14 DAY TRIAL // 