A large malvertising operation involving ads from Google distributed by Bulgarian reseller EngageLab has been discovered by security researchers to redirect visitors to browser-based attack tool Nuclear, which exploits vulnerabilities in outdated plug-ins.
The campaign was spotted on Tuesday by experts at Fox-IT, who believe that the reseller has been compromised by cybercriminals.
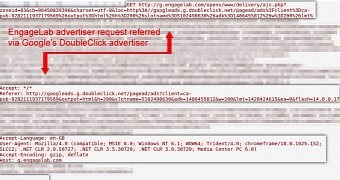
Intermediary domain used in the redirect routine
According to their analysis, the version of Nuclear exploit kit (EK) employed by the attackers attempts to take advantage of vulnerabilities in outdated versions of Adobe Flash Player, Java and Microsoft Silverlight.
Fox-IT security researcher Maarten van Dantzig says in a blog post that the malicious ads first lead to an intermediary website, which then redirects to a domain hosting Nuclear EK.
The investigation revealed that the domains are constantly changing, a tactic used by the cybercriminals to evade detection and prolong the lifespan of the nefarious operation.
Some of the domains Nuclear is foisted from are “banking.techpool.org” with the IP address 62.76.44.174, and “soaring.betsystemreviews.com,” available from 62.76.44.174. Another website seen involved in malvertising is “supervision.sactown.us,” but at the moment, this one is offline.
Outdated plug-ins are the weak spot sought by malvertising attacks
Dantzig says that the nature of the malware delivered through the plug-in exploit has not been identified, but researchers discovered the command and control (C&C) server it used: “alfiantoys.com/wp-news.php” at IP address 174.36.217.82, which appears to be in the US.
Google was alerted about the issue and it may have taken the necessary action to thwart the cybercriminal efforts, because 7 hours after spotting the campaign, the security company no longer recorded malicious redirects from the Bulgarian reseller.
A strong recommendation for users to keep safe from any malvertising campaign is to update their browser plug-ins to the latest versions. Attacks of this kind happen invisibly, and unless the antivirus kicks in and blocks the malware, this can be added without any sign of suspicious activity.
 14 DAY TRIAL //
14 DAY TRIAL //