Taiwan’s Criminal Investigation Bureau (CIB) has arrested one individual suspected of being involved in cyberattacks that leverage the notorious Ghost RAT family.
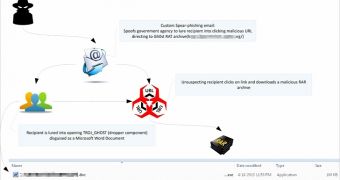
According to Trend Micro, which assisted the CIB in the investigation, the cybercriminals distributed a version of Ghost RAT (BKDR_GHOST) with the aid of spear phishing emails that purported to come from the Taiwan Bureau of National Health Insurance.
The malicious emails contained links that led users to a website designed to push an official-looking RAR archive file.
The archive contained an executable file disguised as a harmless document.
Once run, the file dropped and executed the RAT, allowing cybercriminals to gain complete control of the targeted device.
In addition to luring victims to a malware-serving website, the cybercriminals employ another evasion technique. The final Ghost RAT payloads are held in a password-protected file, the password being stored in an installation script called AMICROSOFT.VBS.
 14 DAY TRIAL //
14 DAY TRIAL //