Security researchers have found that a Citadel campaign that evaded the Microsoft takedown in June 2013 is now using GameOver Trojan and is still claiming victims.
The transition seems to have occurred before the disruption of the GameOver Zeus trojan, dubbed Operation Tovar, that involved a large number of security companies, researchers and law enforcement agencies in the U.S. and Europe.
Apart from infostealing capabilities, the GameOver Zeus botnet also included ransomware components (CryptoLocker) that encrypted files on the computer and demanded payment for unlocking them.
Arbor Networks security firm says in a blog post that the activity of the new GameOver campaign is based on the GameOver Trojan and continues the malicious activity of a Citadel campaign that ended towards the end of 2013.
Cybercriminals rely on malware building software that has a unique key that distinguishes the different versions of the builder, which is used by researchers to identify various malicious campaigns.
It appears that the crooks behind the Citadel campaign were using a builder version whose key (5CB682C10440B2EBAF9F28C1FE438468) was not among those associated with any of the 82 parties accused in the Microsoft’s Citadel botnet lawsuit.
At that time, Microsoft, in cooperation with leaders in the financial services industry and various technology industry partners, managed to take down over 1,000 botnets used to steal banking credentials from the victims.
Based on their research, Arbor Networks determined that after its activity started to ebb in December 2013, this particular Citadel campaign switched to using GameOver Trojan.
Evidence in this sense consists of code that has been modified to work with GameOver, as well as a number of financial institutions from Netherlands and Germany targeted in both campaigns.
The post says that the coding style along with the formatting of the webinjects “looked to have been retrofitted from Citadel to work with Gameover.”
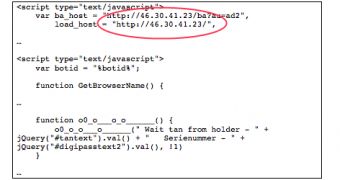
Furthermore, they found that an IP address (46.30.41.23) used for leaking the information from the victims in the new attack had also been used to host a command and control panel for the Citadel campaign.
The security researchers from Arbor Networks conclude that “so far, it seems as if this threat actor has escaped the clutches of the great Citadel take-down and, since the drop site is still receiving stolen credentials, has evaded the Zeus Gameover take-down as well. In the spirit of ‘see something, say something’ and with the recency of the legal action, ASERT has provided the data available to our law enforcement contacts.”
 14 DAY TRIAL //
14 DAY TRIAL //