Japan’s Defense Ministry decided that enough is enough and commissioned Fujitsu Ltd to create a powerful computer virus that’s able to track, identify and neutralize the sources of a cyberattack.
After in the past year many government institutions and companies that handled sensitive information were highly targeted by hackers, Japan came up with a plan that partly imitates the United States and China, states that already use cyber weapons, Daily Yomiuri reports.
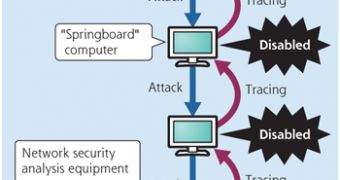
While Japanese state officials say that the virus’ main purpose is to defend the country’s infrastructure and sensitive networks, Fujitsu has been given $2.3 million (1.61 million EUR) to develop something that can trace all the sources of a cyberattack, disable them, and gather relevant information.
The new software should be able to accurately identify the source of a distributed denial of service (DDoS) attack, but also cybercriminal operations aimed to steal sensitive information.
However, current Japanese legislation doesn’t permit the use of cyberweapons against external parties and even the development of a computer virus is against the law.
Some members of the government believe that anti-cyber-attack weapons should be encapsulated into legislation, but Defense Ministry officials state that the program is purposed for defensive uses only.
Senior technology consultant at Sophos, Graham Cluley, reports that such anti-virus viruses are never a good idea, mainly due to the fact that viral code is hard to contain and it can only cause more issues for the IT departments of companies that rely on it.
The expert claims that for such a good virus to deliver positive benefits it wouldn’t need to be viral.
“Anything which can be done by viral code can be done - with less headaches - by non-replicating software,” Cluley says.
“When you're trying to gather digital forensic evidence as to what has broken into your network, and what data it may have stolen, it's probably not wise to let loose a program that starts to trample over your hard drives, making changes.”
 14 DAY TRIAL //
14 DAY TRIAL //