CryptoFortress, a new ransomware with file-encryption capabilities identified in the wild, shares common ground with TorrentLocker, but the internal mechanism shows a different breed of malware.
The ransom message displayed to the victim after data on the computer has been encrypted is the same as in the case of TorrentLocker, which borrowed it from CryptoLocker; similarities have been found in the actual payment page, too.
CryptoFortress relies on Microsoft CryptoAPI for encryption
Security researchers say that the operators of CryptoFortress took the HTML templates and the CSS code from TorrentLocker.
However, the shared resources stop at this, since the code and the encryption scheme available in the new ransomware, as well as the distribution method, are not the same.
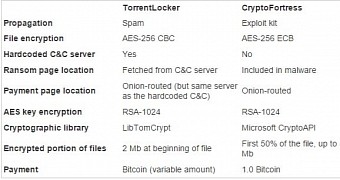
ESET researchers created a list with the common parts present in the two file encrypting malware pieces, and except for the encryption algorithm (AES-256, although in different modes), the encryption of the AES key (RSA-1024) and the fact that the location of the payment is hidden in TOR anonymity network, not much is shared.
CryptoFortress has been seen to be delivered through exploit kits, not spam messages, and the ransom page location is present in the malware code, not retrieved from the command and control (C&C) server.
Furthermore, the cryptographic library used by CryptoFortress is Microsoft’s CryptoAPI, while TorrentLocker relies on the open-source LibTomCrypt.
Another difference consists in the fact that the new malware piece encrypts the first half of the file or up to 5MB and the ransom is of $500 / €465, payable in Bitcoin digital currency.
File encryption key stored locally, secured using public-key cryptography
The first report of CryptoFortress appeared at the beginning of the month from malware researcher Kafeine, who tracks changes in exploit kits. An indicator of the infection is that files have their extension changed to “FRTRSS.”
An analysis from security researchers at France-based security company Lexsi revealed that the AES key used for encrypting the data on the hard drive was stored locally in the HTML ransom files (named “READ IF YOU WANT YOUR FILES BACK”), protected by strong public-key cryptosystems (RSA 1024).
Apart from local drives, the ransomware also impacts mapped drives and network shares and it destroys volume shadow copies in order to prevent restoring the files.
According to the experts, getting the decryption key is possible if the file encryption procedure is in progress and the user took a snapshot of the memory with the malicious process.
 14 DAY TRIAL //
14 DAY TRIAL //