More details about the global scale of the cyber-espionage game are revealed as a malware piece codenamed Babar has been captured and analyzed by various security experts.
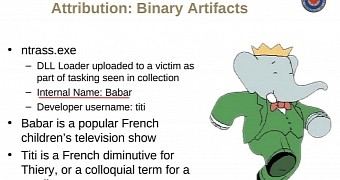
Referenced in files from intelligence agency CSEC (Communications Security Establishment in Canada), leaked in documents from former NSA contractor Edward Snowden, Babar is connected with the espionage activity named Operation Snowglobe.
Sample for the elusive Babar spyware captured
In the documents from CSEC, published by Le Monde and later, less censored, by Der Spiegel, the agency mentions Babar as being part of a state-sponsored operation started by a French intelligence agency.
The purpose of the malware is to capture information from keystrokes, clipboard, as well as taking screenshots and recording audio from conversations over Skype and Yahoo messengers.
Security researchers from GDATA and Cyphort, along with security analyst Marion Marschalek published analysis reports proving that the sample under their scrutiny was in fact the elusive Babar malware that had been searched by the security community since March 2014, when details about Operation Snowglobe first appeared.
One undeniable clue supporting this is the fact that CSEC pointed to a typo made by the malware author (identified in the document as Titi, French diminutive for Thiery) in a user-agent string, where “MSIE” (Microsoft Internet Explorer) was mis-typed as “MSI,” which is present in the Babar version analysed by researchers.
CSEC's attribution remains uncontested
Security researchers say that the malware consists of two parts, a dropper and the Trojan that does the spying.
According to Marschalek, Babar does not feature strong anti-analysis measures. “It is not protected by a runtime packer or crypter, it does not have sandbox detection or anti-debugging measures, most character strings are shown in clear-text,” she says in her analysis.
Cyphort adds more information about the malicious tool revealing two command and control (C&C) servers available in the configuration file. One of them is a legitimate website of an Algerian travel agency that is still online today, while the other is a Turkish domain currently displaying a forbidden access error (403).
Although the common opinion is that Babar is the product of a state-sponsored initiative, the researchers did not make any attribution, GDATA saying that the “assertion of a ‘French intelligence community’ being responsible remains unchanged.”
 14 DAY TRIAL //
14 DAY TRIAL //