Malicious emails carrying Critroni ransomware have been seen to be delivered to management departments at businesses in France.
The cybercriminals seem to be skilled in social engineering as they take precautions to make the messages appear legitimate.
Fake invoice adds Critroni to the computer
First of all, the sender’s address is forged to look like it belongs to a co-worker. In most cases, this is enough to establish an initial level of trust and trick the potential victim into opening the email.
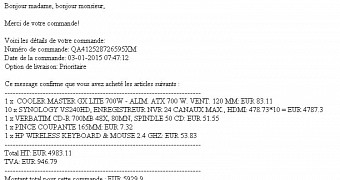
Then, the content of the email is well-crafted and entices the recipient to open the malicious attachment. It purports to be an electronic invoice for about €6,000 / $6,865, accounting the purchase of multiple electronic products.
Security researchers at Bitdefender analyzed the attached file and found it was a CAB file that added the Critroni ransomware to the computer.
Also known as CTB-Locker, the threat has been created to encrypt the information available on the affected system, and on connected storage devices, and ask the victim to pay a fee to receive the key for unlocking the data.
It is unclear if the sample caught by Bitdefender is the current latest variant of Critroni, which comes with an extended period for paying the ransom (96 hours) and has more expensive demands (about 3 BTC which is currently about $656 / €573).
The new strain of the malware also offers trial decryption for five files, to prove the victim that paying would result in getting their files back.
Backups are the safe way to go
Creating backups and storing files in locations not connected to the workstation is the best way to make sure that infection with ransomware that has file encryption capabilities does not have a significant impact. Businesses generally have a backup system set up, but this does not apply in all cases.
By hitting companies instead of regular users, the cybercriminals have a better chance of getting paid if no backup exists, since the encrypted information could be essential for running the business.
However, infection prevention is the best method to avoid unnecessary trouble. Checking the return-path of an email reveals the address of the real sender, and a file claiming to be a document that does not have the appropriate extension but the one for an executable (EXE, CAB, SCR, etc.) is always reason to suspect malicious activity.
 14 DAY TRIAL //
14 DAY TRIAL //