Network administrators now have the possibility to protect their wireless clients from connecting to a rogue access point (AP) by using a tool that discovers and brings them down.
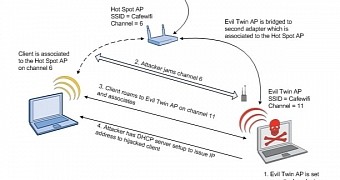
EvilAP Defender application can come in handy in Evil Twin attacks, which consist in impersonating a legitimate Wi-Fi, tricking users into connecting to a device controlled by cybercriminals.
Three detection modes are available
The tool was developed by Mohamed Idris, who says that he included functionality allowing the administrator to run denial-of-service activity against the malicious device, in order to gain more time to set up stronger defenses.
Different access points can be distinguished through identifiers, attributes and tagged parameters (additional values sent along with the beacon frame), and EvilAP Defender relies on these characteristics to determine an impersonating device.
Network administrators can configure the application to take into consideration only the BSSID (basic service set identifier), they can include various attributes (channel, cipher, privacy protocol, and authentication), or they can also add the organizationally unique identifier (OUI) into the mix.
Idris says that at the moment there is no software-based access point that permits changing the tagged parameters, so the third option seems like the best choice for making sure rogue devices do not duplicate the characteristics of a legitimate one.
Admins can get emails when rogue APs are detected
He also informs that the DoS attack function of the tool comes with safety measures and can only be used on APs with the same SSID (service set ID) and a different BSSID or a different frequency channel; otherwise, the network administrator would end up hitting their own devices.
Another feature available in EvilAP Defender is the possibility to alert the admin via email (SMS support to be added) whenever a malicious device is detected.
A “learning mode” that permits whitelisting valid devices is also present in the app. When activated, the tool scans for wireless networks and highlights with green the legitimate ones.
The list of requirements for running EvilAP Defender includes Aircrack-ng suite with a supported wireless network card, MySQL and Python. The tool is available for download on GitHub.
 14 DAY TRIAL //
14 DAY TRIAL //