As promised at the end of July 2010, when Microsoft announced the next iteration of a security toolkit designed to help customers bulletproof arbitrary applications, Enhanced Mitigation Experience Toolkit 2.0 is now available for download. EMET 2.0 is obviously the successor of version 1.0 of the tool, but evolved, guaranteed to bring a little extra kick to customers’ security game.
When talking about the tool, the Redmond company always emphasized that the release is designed to enable users to easily add security mitigation technologies to arbitrary applications.
“This helps prevent vulnerabilities in those applications (especially line of business and 3rd party apps) from successfully being exploited,” revealed Andrew Roths, Sr. Security Development Lead and Fermin J. Serna, Software Development Engineer.
“By deploying these mitigation technologies on legacy products, the tool can also help customers manage risk while they are in the process of transitioning over to modern, more secure products".
“In addition, it makes it easy for customers to test mitigations against any software and provide feedback on their experience to the vendor.”
Just to be clear, EMET 2.0 is in no way a silver bullet solution to application security. Nor is it an alternative to good designed through applying the Security Development Lifecycle best practices when building apps.
But in accordance with the toolkit’s official label, its purpose is to introduce mitigations to security issues. EMET does in no way resolve any security vulnerabilities, but adds the necessary protection mechanisms to fend off exploits and attacks.
“Even with increased community collaboration and information sharing, online criminals are constantly casing systems and applications for vulnerabilities,” noted Jerry Bryant, group manager, Trustworthy Computing, Microsoft.
“Add to that, threats are continuing to move up the stack to applications – many of which don’t have defense-in-depth mitigations".
“So how do you protect your software or applications from unknown vulnerabilities that may or may not exist? One option is to use security mitigations. That’s where EMET comes in,” he said.
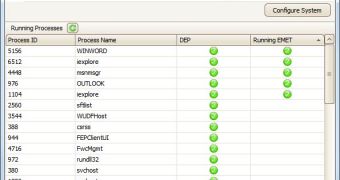
According to the Redmond company, EMET 2.0 supports the following mitigations: Dynamic Data Execution Prevention (DEP); Structure Exception Handler Overwrite Protection (SEHOP); Heap Spray Allocation; Null Page Allocation; Export Address Table Access Filtering; and Mandatory Address Space Layout Randomization (ASLR).
A more comprehensive description of EMET 2.0 is available via this link. Microsoft also offers customer a User Guide.
And last, but definitely not least, the software giant put together a video detailing EMET 2.0 for customers.
 14 DAY TRIAL //
14 DAY TRIAL //